The Dark Side of Open Source: When Community Projects Go Rogue
Open source software is amazing, right? It’s built by communities, shared freely, and powers so much of the internet and our daily tech. Think of it like a huge potluck dinner where everyone brings their best dish to share. It’s all about collaboration, transparency, and making great tools accessible to everyone.
But just like any good thing, there can be a flip side. Sometimes, even in the friendly world of open source, things can go a little sideways. Let’s talk about some of those less-than-ideal situations and what they mean for us.
1. When Trust is Broken: Malicious Code Sneaks In
Imagine you’re using a popular open-source tool that thousands of people rely on. What if, one day, someone – either an original developer or a new contributor – secretly adds a tiny piece of code that does something harmful? This has happened before.
One famous example involved a widely used JavaScript library. A new maintainer was added, and they subtly introduced a piece of code that would steal cryptocurrency from users of a specific application that depended on this library. It was very sneaky because it looked like a normal update.
How it might look (simplified example of suspicious code):
def process_data(user_input):
# ... lots of normal code ...
if some_condition:
# This line might look innocent, but could be sending data elsewhere
send_to_external_server(user_input)
# ... more normal code ...
This kind of attack is tough to spot because it relies on the trust we place in project maintainers. It reminds us that even in open communities, vigilance is key.
2. The Abandoned Project: When Code Gets Lonely
Developers are busy people, and sometimes, life happens. A project that was once actively maintained might slowly fade away. The original creators move on, and no one steps up to take their place. This leaves the software unmaintained.
Why is this a problem? Because new security vulnerabilities are discovered all the time. If a piece of software isn’t updated to fix these flaws, it becomes a ticking time bomb. It’s like leaving your house door unlocked in a neighborhood where new types of locks are invented every week.
Think about the “Heartbleed” bug. It was a serious vulnerability found in a widely used open-source encryption library. While it was eventually fixed, it highlighted how critical it is for foundational open-source projects to be actively maintained and audited.

If you’re using an unmaintained library, you might be unknowingly exposing yourself or your users to risks that have known solutions, but no one is applying them to that specific project.
3. Supply Chain Attacks: The Domino Effect
Most modern software isn’t built from scratch. It relies on hundreds, sometimes thousands, of smaller open-source components, like building blocks. This is called a “supply chain.” If one of these tiny building blocks is compromised, it can affect every piece of software that uses it.
Attackers are getting smarter. Instead of trying to hack a big company directly, they might target a small, obscure open-source library that the big company uses. If they can inject malicious code into that small library, it automatically gets pulled into the big company’s software when they update their dependencies.
How you might check dependencies (conceptual command):
# For Node.js projects
npm audit
# For Python projects
pip check
# These commands help you see if your project uses libraries with known vulnerabilities.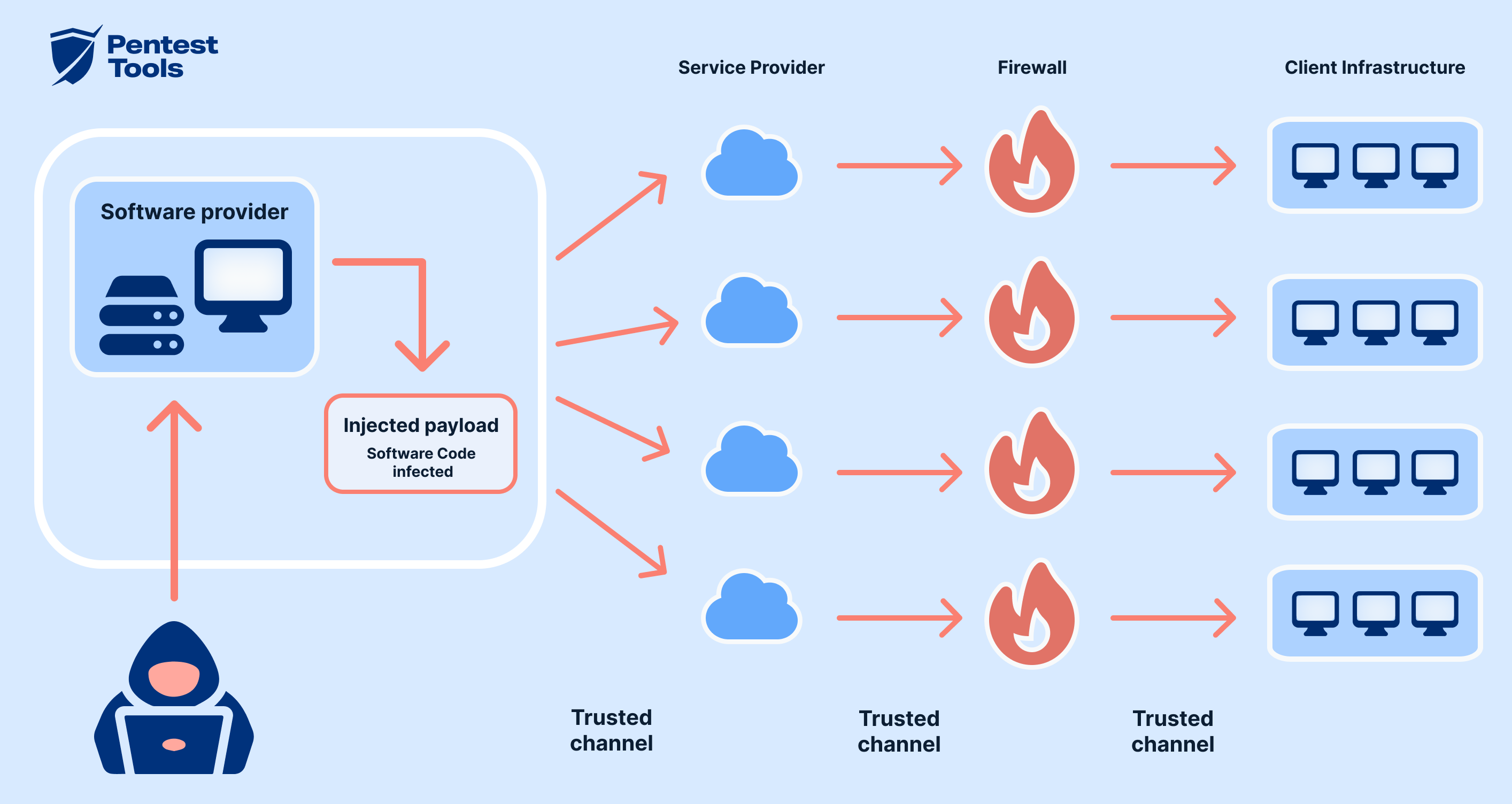
This is a growing concern because it’s hard to keep track of every single component in a complex software system.
4. What Can We Do? Staying Safe in the Open Source World
Don’t get us wrong, open source is still fantastic! These issues are rare, but it’s good to be aware. Here’s how we can all help keep the open-source ecosystem healthy and safe:
For Users (if you use open-source software):
- Check the Reputation: Before using a new open-source tool, see how active its community is, how often it’s updated, and if it has a good reputation.
- Stay Updated: Always use the latest versions of software. Updates often include crucial security fixes.
- Use Trusted Sources: Download software from official repositories or well-known platforms.
For Developers (if you contribute to or build with open source):
- Code Reviews: Always have multiple eyes on new code, especially from new contributors.
- Security Audits: Regularly scan your dependencies for known vulnerabilities.
- Be Responsible: If you find a vulnerability in an open-source project, report it responsibly to the maintainers first, giving them time to fix it before making it public.
- Support Maintainers: If you rely on a project, consider contributing back, even if it’s just reporting bugs or helping with documentation. Active communities are safer communities.

Conclusion
The open-source world is a testament to human collaboration and innovation. While there are “dark sides” where trust can be broken or projects left behind, understanding these risks helps us navigate the landscape more safely. By being aware, staying vigilant, and supporting the community, we can continue to enjoy the immense benefits that open source brings to our digital lives.
Keep exploring, keep learning, and stay safe out there!
Blog post & guide © havoc 2025- For educational purposes only.
Tag or DM me if you learned something.!

Comments