Hey friends ,am happy your here ,thanks for that,so yeah this time i had the opportunity to participate in nahamcon winter ctf playing with team static_9 and below is a short writeup of some questions i managed to solve. The language or tone may be not perfect so dont mind it 🙏🏻…

1. Linear Lines
Challenge Description
The challenge provided a ciphertext and a hint:
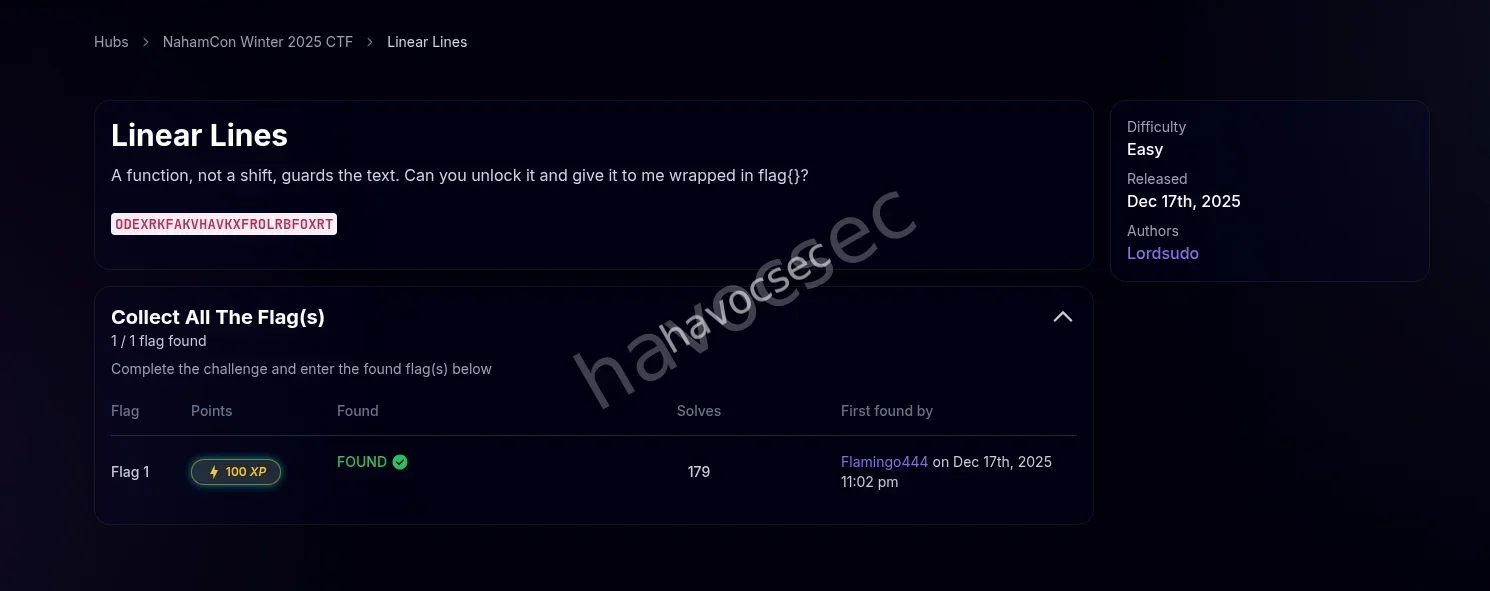
Ciphertext:
ODEXRKFAKVHAVKXFROLRBFOXRTHint: A function, not a shift, guards the text. Can you unlock it and give it to me wrapped in flag{}?
Step 1: Analysis and Hypothesis
The hint “Linear Lines” and “A function, not a shift” strongly suggests a Linear Cipher or, more specifically, an Affine Cipher.
Shift Ciphers(like Caesar) use a simple addition function: E(x) = (x + b) \pmod{26}Affine Ciphersuse a linear function: E(x) = (ax + b) \pmod{26}, where a and b are the keys, and a must be coprime to 26 (i.e., a \in {1, 3, 5, 7, 9, 11, 15, 17, 19, 21, 23, 25}).
Since there are 12 possible values for a and 26 possible values for b, there are 12 \times 26 = 312 possible keys. This is a small enough number for a brute-force attack.
Step 2: Brute-Force Script Implementation
I asked my buddy chatgpt to create a Python script, affine_solver.py, to iterate through all 312 possible key pairs (a, b) and attempt decryption.
The decryption function is defined as D(y)=a−1(y−b) mod 26D(y) = a^{-1}(y - b) \bmod 26D(y)=a−1(y−b)mod26, where a−1a^{-1}a−1 is the modular multiplicative inverse of a modulo 26.
Input: affine_solver.py
# affine_solver.py
CIPHERTEXT = "ODEXRKFAKVHAVKXFROLRBFOXRT"
ALPHABET = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"
# Modular multiplicative inverses for a mod 26
INVERSES = {
1: 1, 3: 9, 5: 21, 7: 15, 9: 3, 11: 19, 15: 7, 17: 23, 19: 11, 21: 5, 23: 17, 25: 25
}
def decrypt(ciphertext, a, b):
"""Decrypts a ciphertext using the Affine Cipher with keys a and b."""
if a not in INVERSES:
return "Invalid 'a' key (must be coprime to 26)"
a_inv = INVERSES[a]
plaintext = ""
for char in ciphertext:
if 'A' <= char <= 'Z':
y = ALPHABET.index(char)
# D(y) = a_inv * (y - b) mod 26
x = (a_inv * (y - b)) % 26
plaintext += ALPHABET[x]
else:
plaintext += char # Keep non-alphabetic characters as is
return plaintext
def solve_affine(ciphertext):
"""Brute-forces all possible Affine Cipher keys."""
results = []
# Iterate through all valid 'a' keys
for a in INVERSES.keys():
# Iterate through all possible 'b' keys (0 to 25)
for b in range(26):
plaintext = decrypt(ciphertext, a, b)
results.append(f"a={a:02}, b={b:02}: {plaintext}")
return results
if __name__ == "__main__":
# ... (Code to run solver and save to decryption_results.txt)
all_results = solve_affine(CIPHERTEXT)
with open("decryption_results.txt", "w") as f:
for line in all_results:
f.write(line + "\n")Step 3: Execution and Output Generation
Executed the script , and the results were saved to a file named decryption_results.txt.
Input: Shell Command
python3 affine_solver.pyOutput: Shell Log (Partial)
havoc@parrot:~ $ python3 affine_solver.py
Ciphertext: ODEXRKFAKVHAVKXFROLRBFOXRT
Decryption complete. Results saved to decryption_results.txt. Total 312 attempts.
First 10 results:
a=01, b=00: ODEXRKFAKVHAVKXFROLRBFOXRT
a=01, b=01: NCDWQJEZJUGZUJWEQNKQAENWQS
a=01, b=02: MBCVPIDYITFYTIVDPMJPZDMVPR
...Step 4: Review of Decryption Results
The decryption_results.txt file was reviewed to find a meaningful English phrase.
decryption_results.txt
cat decryption_results.txt
a=01, b=00: ODEXRKFAKVHAVKXFROLRBFOXRT
a=01, b=01: NCDWQJEZJUGZUJWEQNKQAENWQS
a=01, b=02: MBCVPIDYITFYTIVDPMJPZDMVPR
a=01, b=03: LABUOHCXHSEXSHUCOLIOYCLUOQ
a=01, b=04: KZATNGBWGRDWRGTBNKHNXBKTNP
a=01, b=05: JYZSMFAVFQCVQFSAMJGMWAJSMO
a=01, b=06: IXYRLEZUEPBUPERZLIFLVZIRLN
a=01, b=07: HWXQKDYTDOATODQYKHEKUYHQKM
a=01, b=08: GVWPJCXSCNZSNCPXJGDJTXGPJL
a=01, b=09: FUVOIBWRBMYRMBOWIFCISWFOIK
a=01, b=10: ETUNHAVQALXQLANVHEBHRVENHJ
a=01, b=11: DSTMGZUPZKWPKZMUGDAGQUDMGI
a=01, b=12: CRSLFYTOYJVOJYLTFCZFPTCLFH
a=01, b=13: BQRKEXSNXIUNIXKSEBYEOSBKEG
a=01, b=14: APQJDWRMWHTMHWJRDAXDNRAJDF
a=01, b=15: ZOPICVQLVGSLGVIQCZWCMQZICE
a=01, b=16: YNOHBUPKUFRKFUHPBYVBLPYHBD
a=01, b=17: XMNGATOJTEQJETGOAXUAKOXGAC
a=01, b=18: WLMFZSNISDPIDSFNZWTZJNWFZB
a=01, b=19: VKLEYRMHRCOHCREMYVSYIMVEYA
a=01, b=20: UJKDXQLGQBNGBQDLXURXHLUDXZ
a=01, b=21: TIJCWPKFPAMFAPCKWTQWGKTCWY
a=01, b=22: SHIBVOJEOZLEZOBJVSPVFJSBVX
a=01, b=23: RGHAUNIDNYKDYNAIUROUEIRAUW
a=01, b=24: QFGZTMHCMXJCXMZHTQNTDHQZTV
a=01, b=25: PEFYSLGBLWIBWLYGSPMSCGPYSU
a=03, b=00: WBKZXMTAMHLAHMZTXWVXJTWZXP
a=03, b=01: NSBQODKRDYCRYDQKONMOAKNQOG
a=03, b=02: EJSHFUBIUPTIPUHBFEDFRBEHFX
a=03, b=03: VAJYWLSZLGKZGLYSWVUWISVYWO
a=03, b=04: MRAPNCJQCXBQXCPJNMLNZJMPNF
a=03, b=05: DIRGETAHTOSHOTGAEDCEQADGEW
a=03, b=06: UZIXVKRYKFJYFKXRVUTVHRUXVN
a=03, b=07: LQZOMBIPBWAPWBOIMLKMYILOME
a=03, b=08: CHQFDSZGSNRGNSFZDCBDPZCFDV
a=03, b=09: TYHWUJQXJEIXEJWQUTSUGQTWUM
a=03, b=10: KPYNLAHOAVZOVANHLKJLXHKNLD
a=03, b=11: BGPECRYFRMQFMREYCBACOYBECU
a=03, b=12: SXGVTIPWIDHWDIVPTSRTFPSVTL
a=03, b=13: JOXMKZGNZUYNUZMGKJIKWGJMKC
a=03, b=14: AFODBQXEQLPELQDXBAZBNXADBT
a=03, b=15: RWFUSHOVHCGVCHUOSRQSEORUSK
a=03, b=16: INWLJYFMYTXMTYLFJIHJVFILJB
a=03, b=17: ZENCAPWDPKODKPCWAZYAMWZCAS
a=03, b=18: QVETRGNUGBFUBGTNRQPRDNQTRJ
a=03, b=19: HMVKIXELXSWLSXKEIHGIUEHKIA
a=03, b=20: YDMBZOVCOJNCJOBVZYXZLVYBZR
a=03, b=21: PUDSQFMTFAETAFSMQPOQCMPSQI
a=03, b=22: GLUJHWDKWRVKRWJDHGFHTDGJHZ
a=03, b=23: XCLAYNUBNIMBINAUYXWYKUXAYQ
a=03, b=24: OTCRPELSEZDSZERLPONPBLORPH
a=03, b=25: FKTIGVCJVQUJQVICGFEGSCFIGY
a=05, b=00: ILGPTCBACZRAZCPBTIXTVBIPTJ
a=05, b=01: NQLUYHGFHEWFEHUGYNCYAGNUYO
a=05, b=02: SVQZDMLKMJBKJMZLDSHDFLSZDT
a=05, b=03: XAVEIRQPROGPOREQIXMIKQXEIY
a=05, b=04: CFAJNWVUWTLUTWJVNCRNPVCJND
a=05, b=05: HKFOSBAZBYQZYBOASHWSUAHOSI
a=05, b=06: MPKTXGFEGDVEDGTFXMBXZFMTXN
a=05, b=07: RUPYCLKJLIAJILYKCRGCEKRYCS
a=05, b=08: WZUDHQPOQNFONQDPHWLHJPWDHX
a=05, b=09: BEZIMVUTVSKTSVIUMBQMOUBIMC
a=05, b=10: GJENRAZYAXPYXANZRGVRTZGNRH
a=05, b=11: LOJSWFEDFCUDCFSEWLAWYELSWM
a=05, b=12: QTOXBKJIKHZIHKXJBQFBDJQXBR
a=05, b=13: VYTCGPONPMENMPCOGVKGIOVCGW
a=05, b=14: ADYHLUTSURJSRUHTLAPLNTAHLB
a=05, b=15: FIDMQZYXZWOXWZMYQFUQSYFMQG
a=05, b=16: KNIRVEDCEBTCBERDVKZVXDKRVL
a=05, b=17: PSNWAJIHJGYHGJWIAPEACIPWAQ
a=05, b=18: UXSBFONMOLDMLOBNFUJFHNUBFV
a=05, b=19: ZCXGKTSRTQIRQTGSKZOKMSZGKA
a=05, b=20: EHCLPYXWYVNWVYLXPETPRXELPF
a=05, b=21: JMHQUDCBDASBADQCUJYUWCJQUK
a=05, b=22: ORMVZIHGIFXGFIVHZODZBHOVZP
a=05, b=23: TWRAENMLNKCLKNAMETIEGMTAEU
a=05, b=24: YBWFJSRQSPHQPSFRJYNJLRYFJZ
a=05, b=25: DGBKOXWVXUMVUXKWODSOQWDKOE
a=07, b=00: CTIHVUXAUDBADUHXVCJVPXCHVZ
a=07, b=01: NETSGFILFOMLOFSIGNUGAINSGK
a=07, b=02: YPEDRQTWQZXWZQDTRYFRLTYDRV
a=07, b=03: JAPOCBEHBKIHKBOECJQCWEJOCG
a=07, b=04: ULAZNMPSMVTSVMZPNUBNHPUZNR
a=07, b=05: FWLKYXADXGEDGXKAYFMYSAFKYC
a=07, b=06: QHWVJILOIRPORIVLJQXJDLQVJN
a=07, b=07: BSHGUTWZTCAZCTGWUBIUOWBGUY
a=07, b=08: MDSRFEHKENLKNERHFMTFZHMRFJ
a=07, b=09: XODCQPSVPYWVYPCSQXEQKSXCQU
a=07, b=10: IZONBADGAJHGJANDBIPBVDINBF
a=07, b=11: TKZYMLORLUSRULYOMTAMGOTYMQ
a=07, b=12: EVKJXWZCWFDCFWJZXELXRZEJXB
a=07, b=13: PGVUIHKNHQONQHUKIPWICKPUIM
a=07, b=14: ARGFTSVYSBZYBSFVTAHTNVAFTX
a=07, b=15: LCRQEDGJDMKJMDQGELSEYGLQEI
a=07, b=16: WNCBPORUOXVUXOBRPWDPJRWBPT
a=07, b=17: HYNMAZCFZIGFIZMCAHOAUCHMAE
a=07, b=18: SJYXLKNQKTRQTKXNLSZLFNSXLP
a=07, b=19: DUJIWVYBVECBEVIYWDKWQYDIWA
a=07, b=20: OFUTHGJMGPNMPGTJHOVHBJOTHL
a=07, b=21: ZQFESRUXRAYXAREUSZGSMUZESW
a=07, b=22: KBQPDCFICLJILCPFDKRDXFKPDH
a=07, b=23: VMBAONQTNWUTWNAQOVCOIQVAOS
a=07, b=24: GXMLZYBEYHFEHYLBZGNZTBGLZD
a=07, b=25: RIXWKJMPJSQPSJWMKRYKEMRWKO
a=09, b=00: QJMRZEPAELVALERPZQHZDPQRZF
a=09, b=01: NGJOWBMXBISXIBOMWNEWAMNOWC
a=09, b=02: KDGLTYJUYFPUFYLJTKBTXJKLTZ
a=09, b=03: HADIQVGRVCMRCVIGQHYQUGHIQW
a=09, b=04: EXAFNSDOSZJOZSFDNEVNRDEFNT
a=09, b=05: BUXCKPALPWGLWPCAKBSKOABCKQ
a=09, b=06: YRUZHMXIMTDITMZXHYPHLXYZHN
a=09, b=07: VORWEJUFJQAFQJWUEVMEIUVWEK
a=09, b=08: SLOTBGRCGNXCNGTRBSJBFRSTBH
a=09, b=09: PILQYDOZDKUZKDQOYPGYCOPQYE
a=09, b=10: MFINVALWAHRWHANLVMDVZLMNVB
a=09, b=11: JCFKSXITXEOTEXKISJASWIJKSY
a=09, b=12: GZCHPUFQUBLQBUHFPGXPTFGHPV
a=09, b=13: DWZEMRCNRYINYRECMDUMQCDEMS
a=09, b=14: ATWBJOZKOVFKVOBZJARJNZABJP
a=09, b=15: XQTYGLWHLSCHSLYWGXOGKWXYGM
a=09, b=16: UNQVDITEIPZEPIVTDULDHTUVDJ
a=09, b=17: RKNSAFQBFMWBMFSQARIAEQRSAG
a=09, b=18: OHKPXCNYCJTYJCPNXOFXBNOPXD
a=09, b=19: LEHMUZKVZGQVGZMKULCUYKLMUA
a=09, b=20: IBEJRWHSWDNSDWJHRIZRVHIJRX
a=09, b=21: FYBGOTEPTAKPATGEOFWOSEFGOU
a=09, b=22: CVYDLQBMQXHMXQDBLCTLPBCDLR
a=09, b=23: ZSVAINYJNUEJUNAYIZQIMYZAIO
a=09, b=24: WPSXFKVGKRBGRKXVFWNFJVWXFL
a=09, b=25: TMPUCHSDHOYDOHUSCTKCGSTUCI
a=11, b=00: GFYVLIRAIJDAJIVRLGBLTRGVLX
a=11, b=01: NMFCSPYHPQKHQPCYSNISAYNCSE
a=11, b=02: UTMJZWFOWXROXWJFZUPZHFUJZL
a=11, b=03: BATQGDMVDEYVEDQMGBWGOMBQGS
a=11, b=04: IHAXNKTCKLFCLKXTNIDNVTIXNZ
a=11, b=05: POHEURAJRSMJSREAUPKUCAPEUG
a=11, b=06: WVOLBYHQYZTQZYLHBWRBJHWLBN
a=11, b=07: DCVSIFOXFGAXGFSOIDYIQODSIU
a=11, b=08: KJCZPMVEMNHENMZVPKFPXVKZPB
a=11, b=09: RQJGWTCLTUOLUTGCWRMWECRGWI
a=11, b=10: YXQNDAJSABVSBANJDYTDLJYNDP
a=11, b=11: FEXUKHQZHICZIHUQKFAKSQFUKW
a=11, b=12: MLEBROXGOPJGPOBXRMHRZXMBRD
a=11, b=13: TSLIYVENVWQNWVIEYTOYGETIYK
a=11, b=14: AZSPFCLUCDXUDCPLFAVFNLAPFR
a=11, b=15: HGZWMJSBJKEBKJWSMHCMUSHWMY
a=11, b=16: ONGDTQZIQRLIRQDZTOJTBZODTF
a=11, b=17: VUNKAXGPXYSPYXKGAVQAIGVKAM
a=11, b=18: CBURHENWEFZWFERNHCXHPNCRHT
a=11, b=19: JIBYOLUDLMGDMLYUOJEOWUJYOA
a=11, b=20: QPIFVSBKSTNKTSFBVQLVDBQFVH
a=11, b=21: XWPMCZIRZAURAZMICXSCKIXMCO
a=11, b=22: EDWTJGPYGHBYHGTPJEZJRPETJV
a=11, b=23: LKDAQNWFNOIFONAWQLGQYWLAQC
a=11, b=24: SRKHXUDMUVPMVUHDXSNXFDSHXJ
a=11, b=25: ZYROEBKTBCWTCBOKEZUEMKZOEQ
a=15, b=00: UVCFPSJASRXARSFJPUZPHJUFPD
a=15, b=01: NOVYILCTLKQTKLYCINSIACNYIW
a=15, b=02: GHORBEVMEDJMDERVBGLBTVGRBP
a=15, b=03: ZAHKUXOFXWCFWXKOUZEUMOZKUI
a=15, b=04: STADNQHYQPVYPQDHNSXNFHSDNB
a=15, b=05: LMTWGJARJIORIJWAGLQGYALWGU
a=15, b=06: EFMPZCTKCBHKBCPTZEJZRTEPZN
a=15, b=07: XYFISVMDVUADUVIMSXCSKMXISG
a=15, b=08: QRYBLOFWONTWNOBFLQVLDFQBLZ
a=15, b=09: JKRUEHYPHGMPGHUYEJOEWYJUES
a=15, b=10: CDKNXARIAZFIZANRXCHXPRCNXL
a=15, b=11: VWDGQTKBTSYBSTGKQVAQIKVGQE
a=15, b=12: OPWZJMDUMLRULMZDJOTJBDOZJX
a=15, b=13: HIPSCFWNFEKNEFSWCHMCUWHSCQ
a=15, b=14: ABILVYPGYXDGXYLPVAFVNPALVJ
a=15, b=15: TUBEORIZRQWZQREIOTYOGITEOC
a=15, b=16: MNUXHKBSKJPSJKXBHMRHZBMXHV
a=15, b=17: FGNQADULDCILCDQUAFKASUFQAO
a=15, b=18: YZGJTWNEWVBEVWJNTYDTLNYJTH
a=15, b=19: RSZCMPGXPOUXOPCGMRWMEGRCMA
a=15, b=20: KLSVFIZQIHNQHIVZFKPFXZKVFT
a=15, b=21: DELOYBSJBAGJABOSYDIYQSDOYM
a=15, b=22: WXEHRULCUTZCTUHLRWBRJLWHRF
a=15, b=23: PQXAKNEVNMSVMNAEKPUKCEPAKY
a=15, b=24: IJQTDGXOGFLOFGTXDINDVXITDR
a=15, b=25: BCJMWZQHZYEHYZMQWBGWOQBMWK
a=17, b=00: KROJBWLAWPFAPWJLBKTBXLKJBV
a=17, b=01: NURMEZODZSIDSZMOENWEAONMEY
a=17, b=02: QXUPHCRGCVLGVCPRHQZHDRQPHB
a=17, b=03: TAXSKFUJFYOJYFSUKTCKGUTSKE
a=17, b=04: WDAVNIXMIBRMBIVXNWFNJXWVNH
a=17, b=05: ZGDYQLAPLEUPELYAQZIQMAZYQK
a=17, b=06: CJGBTODSOHXSHOBDTCLTPDCBTN
a=17, b=07: FMJEWRGVRKAVKREGWFOWSGFEWQ
a=17, b=08: IPMHZUJYUNDYNUHJZIRZVJIHZT
a=17, b=09: LSPKCXMBXQGBQXKMCLUCYMLKCW
a=17, b=10: OVSNFAPEATJETANPFOXFBPONFZ
a=17, b=11: RYVQIDSHDWMHWDQSIRAIESRQIC
a=17, b=12: UBYTLGVKGZPKZGTVLUDLHVUTLF
a=17, b=13: XEBWOJYNJCSNCJWYOXGOKYXWOI
a=17, b=14: AHEZRMBQMFVQFMZBRAJRNBAZRL
a=17, b=15: DKHCUPETPIYTIPCEUDMUQEDCUO
a=17, b=16: GNKFXSHWSLBWLSFHXGPXTHGFXR
a=17, b=17: JQNIAVKZVOEZOVIKAJSAWKJIAU
a=17, b=18: MTQLDYNCYRHCRYLNDMVDZNMLDX
a=17, b=19: PWTOGBQFBUKFUBOQGPYGCQPOGA
a=17, b=20: SZWRJETIEXNIXERTJSBJFTSRJD
a=17, b=21: VCZUMHWLHAQLAHUWMVEMIWVUMG
a=17, b=22: YFCXPKZOKDTODKXZPYHPLZYXPJ
a=17, b=23: BIFASNCRNGWRGNACSBKSOCBASM
a=17, b=24: ELIDVQFUQJZUJQDFVENVRFEDVP
a=17, b=25: HOLGYTIXTMCXMTGIYHQYUIHGYS
a=19, b=00: YHSTFGDAGXZAXGTDFYRFLDYTFB
a=19, b=01: NWHIUVSPVMOPMVISUNGUASNIUQ
a=19, b=02: CLWXJKHEKBDEBKXHJCVJPHCXJF
a=19, b=03: RALMYZWTZQSTQZMWYRKYEWRMYU
a=19, b=04: GPABNOLIOFHIFOBLNGZNTLGBNJ
a=19, b=05: VEPQCDAXDUWXUDQACVOCIAVQCY
a=19, b=06: KTEFRSPMSJLMJSFPRKDRXPKFRN
a=19, b=07: ZITUGHEBHYABYHUEGZSGMEZUGC
a=19, b=08: OXIJVWTQWNPQNWJTVOHVBTOJVR
a=19, b=09: DMXYKLIFLCEFCLYIKDWKQIDYKG
a=19, b=10: SBMNZAXUARTURANXZSLZFXSNZV
a=19, b=11: HQBCOPMJPGIJGPCMOHAOUMHCOK
a=19, b=12: WFQRDEBYEVXYVERBDWPDJBWRDZ
a=19, b=13: LUFGSTQNTKMNKTGQSLESYQLGSO
a=19, b=14: AJUVHIFCIZBCZIVFHATHNFAVHD
a=19, b=15: PYJKWXURXOQROXKUWPIWCUPKWS
a=19, b=16: ENYZLMJGMDFGDMZJLEXLRJEZLH
a=19, b=17: TCNOABYVBSUVSBOYATMAGYTOAW
a=19, b=18: IRCDPQNKQHJKHQDNPIBPVNIDPL
a=19, b=19: XGRSEFCZFWYZWFSCEXQEKCXSEA
a=19, b=20: MVGHTUROULNOLUHRTMFTZRMHTP
a=19, b=21: BKVWIJGDJACDAJWGIBUIOGBWIE
a=19, b=22: QZKLXYVSYPRSPYLVXQJXDVQLXT
a=19, b=23: FOZAMNKHNEGHENAKMFYMSKFAMI
a=19, b=24: UDOPBCZWCTVWTCPZBUNBHZUPBX
a=19, b=25: JSDEQROLRIKLIREOQJCQWOJEQM
a=21, b=00: SPULHYZAYBJABYLZHSDHFZSLHR
a=21, b=01: NKPGCTUVTWEVWTGUCNYCAUNGCM
a=21, b=02: IFKBXOPQORZQROBPXITXVPIBXH
a=21, b=03: DAFWSJKLJMULMJWKSDOSQKDWSC
a=21, b=04: YVARNEFGEHPGHERFNYJNLFYRNX
a=21, b=05: TQVMIZABZCKBCZMAITEIGATMIS
a=21, b=06: OLQHDUVWUXFWXUHVDOZDBVOHDN
a=21, b=07: JGLCYPQRPSARSPCQYJUYWQJCYI
a=21, b=08: EBGXTKLMKNVMNKXLTEPTRLEXTD
a=21, b=09: ZWBSOFGHFIQHIFSGOZKOMGZSOY
a=21, b=10: URWNJABCADLCDANBJUFJHBUNJT
a=21, b=11: PMRIEVWXVYGXYVIWEPAECWPIEO
a=21, b=12: KHMDZQRSQTBSTQDRZKVZXRKDZJ
a=21, b=13: FCHYULMNLOWNOLYMUFQUSMFYUE
a=21, b=14: AXCTPGHIGJRIJGTHPALPNHATPZ
a=21, b=15: VSXOKBCDBEMDEBOCKVGKICVOKU
a=21, b=16: QNSJFWXYWZHYZWJXFQBFDXQJFP
a=21, b=17: LINEARSTRUCTURESALWAYSLEAK
a=21, b=18: GDIZVMNOMPXOPMZNVGRVTNGZVF
a=21, b=19: BYDUQHIJHKSJKHUIQBMQOIBUQA
a=21, b=20: WTYPLCDECFNEFCPDLWHLJDWPLV
a=21, b=21: ROTKGXYZXAIZAXKYGRCGEYRKGQ
a=21, b=22: MJOFBSTUSVDUVSFTBMXBZTMFBL
a=21, b=23: HEJAWNOPNQYPQNAOWHSWUOHAWG
a=21, b=24: CZEVRIJKILTKLIVJRCNRPJCVRB
a=21, b=25: XUZQMDEFDGOFGDQEMXIMKEXQMW
a=23, b=00: EZQBDOHAOTPATOBHDEFDRHEBDL
a=23, b=01: NIZKMXQJXCYJCXKQMNOMAQNKMU
a=23, b=02: WRITVGZSGLHSLGTZVWXVJZWTVD
a=23, b=03: FARCEPIBPUQBUPCIEFGESIFCEM
a=23, b=04: OJALNYRKYDZKDYLRNOPNBROLNV
a=23, b=05: XSJUWHATHMITMHUAWXYWKAXUWE
a=23, b=06: GBSDFQJCQVRCVQDJFGHFTJGDFN
a=23, b=07: PKBMOZSLZEALEZMSOPQOCSPMOW
a=23, b=08: YTKVXIBUINJUNIVBXYZXLBYVXF
a=23, b=09: HCTEGRKDRWSDWREKGHIGUKHEGO
a=23, b=10: QLCNPATMAFBMFANTPQRPDTQNPX
a=23, b=11: ZULWYJCVJOKVOJWCYZAYMCZWYG
a=23, b=12: IDUFHSLESXTEXSFLHIJHVLIFHP
a=23, b=13: RMDOQBUNBGCNGBOUQRSQEUROQY
a=23, b=14: AVMXZKDWKPLWPKXDZABZNDAXZH
a=23, b=15: JEVGITMFTYUFYTGMIJKIWMJGIQ
a=23, b=16: SNEPRCVOCHDOHCPVRSTRFVSPRZ
a=23, b=17: BWNYALEXLQMXQLYEABCAOEBYAI
a=23, b=18: KFWHJUNGUZVGZUHNJKLJXNKHJR
a=23, b=19: TOFQSDWPDIEPIDQWSTUSGWTQSA
a=23, b=20: CXOZBMFYMRNYRMZFBCDBPFCZBJ
a=23, b=21: LGXIKVOHVAWHAVIOKLMKYOLIKS
a=23, b=22: UPGRTEXQEJFQJERXTUVTHXURTB
a=23, b=23: DYPACNGZNSOZSNAGCDECQGDACK
a=23, b=24: MHYJLWPIWBXIBWJPLMNLZPMJLT
a=23, b=25: VQHSUFYRFKGRKFSYUVWUIYVSUC
a=25, b=00: MXWDJQVAQFTAFQDVJMPJZVMDJH
a=25, b=01: NYXEKRWBRGUBGREWKNQKAWNEKI
a=25, b=02: OZYFLSXCSHVCHSFXLORLBXOFLJ
a=25, b=03: PAZGMTYDTIWDITGYMPSMCYPGMK
a=25, b=04: QBAHNUZEUJXEJUHZNQTNDZQHNL
a=25, b=05: RCBIOVAFVKYFKVIAORUOEARIOM
a=25, b=06: SDCJPWBGWLZGLWJBPSVPFBSJPN
a=25, b=07: TEDKQXCHXMAHMXKCQTWQGCTKQO
a=25, b=08: UFELRYDIYNBINYLDRUXRHDULRP
a=25, b=09: VGFMSZEJZOCJOZMESVYSIEVMSQ
a=25, b=10: WHGNTAFKAPDKPANFTWZTJFWNTR
a=25, b=11: XIHOUBGLBQELQBOGUXAUKGXOUS
a=25, b=12: YJIPVCHMCRFMRCPHVYBVLHYPVT
a=25, b=13: ZKJQWDINDSGNSDQIWZCWMIZQWU
a=25, b=14: ALKRXEJOETHOTERJXADXNJARXV
a=25, b=15: BMLSYFKPFUIPUFSKYBEYOKBSYW
a=25, b=16: CNMTZGLQGVJQVGTLZCFZPLCTZX
a=25, b=17: DONUAHMRHWKRWHUMADGAQMDUAY
a=25, b=18: EPOVBINSIXLSXIVNBEHBRNEVBZ
a=25, b=19: FQPWCJOTJYMTYJWOCFICSOFWCA
a=25, b=20: GRQXDKPUKZNUZKXPDGJDTPGXDB
a=25, b=21: HSRYELQVLAOVALYQEHKEUQHYEC
a=25, b=22: ITSZFMRWMBPWBMZRFILFVRIZFD
a=25, b=23: JUTAGNSXNCQXCNASGJMGWSJAGE
a=25, b=24: KVUBHOTYODRYDOBTHKNHXTKBHF
a=25, b=25: LWVCIPUZPESZEPCUILOIYULCIG
┌─[havoc@parrot]─[~/Downloads/ctf/nahamsec]
└──╼ $Output: File Content (Excerpt)
The meaningful plaintext was found at line 252:
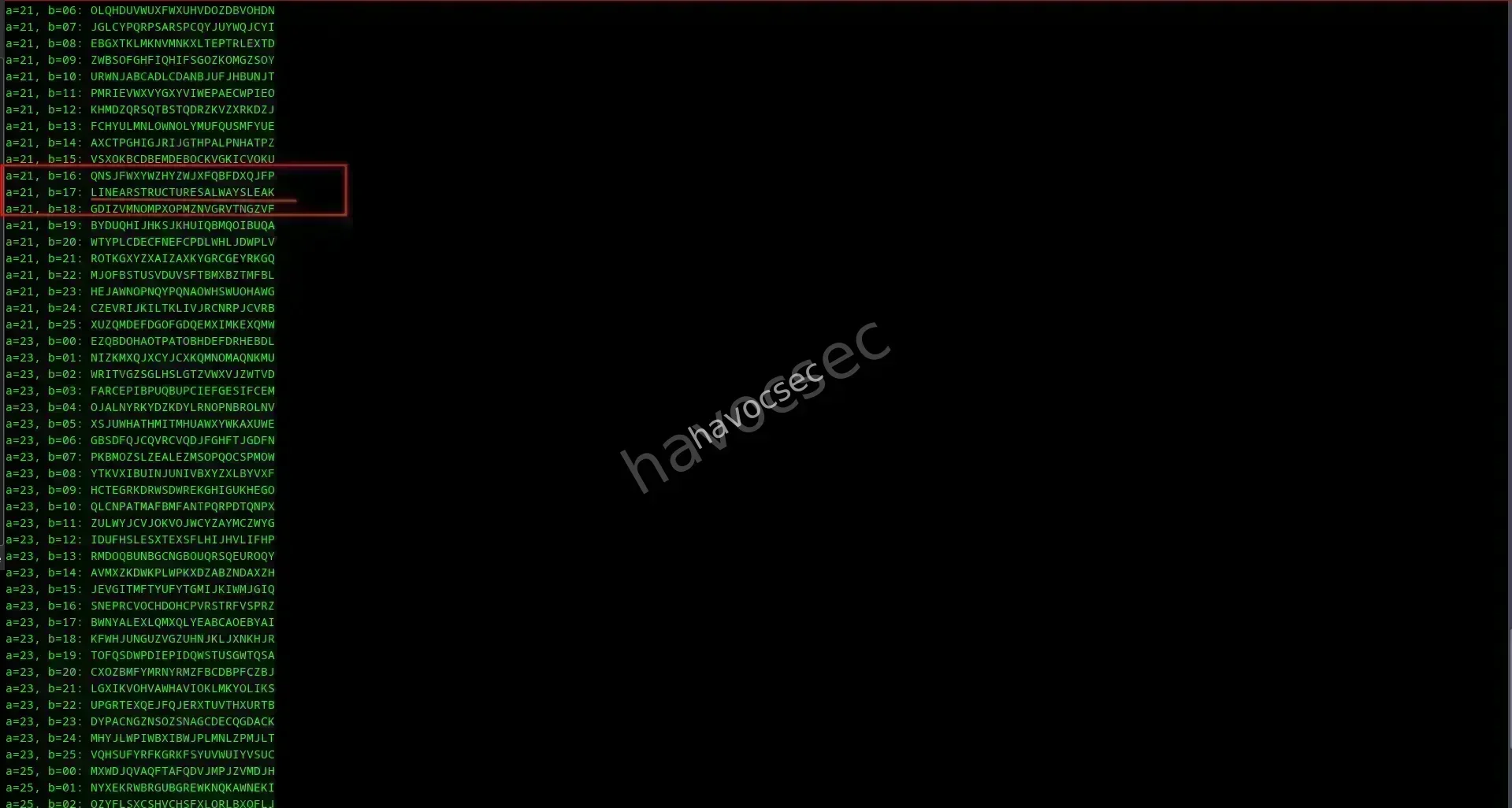
The decrypted message is LINEARSTRUCTURESALWAYSLEAK, which is a clear, coherent phrase and the expected format for this CTF flag.
Step 5: Final Flag
The keys used for decryption were a=21 andb=17.
The final flag, wrapped in the required format, is:
flag{LINEARSTRUCTURESALWAYSLEAK}
The next challenge was this;
2.Reindeer Route
Challenge Overview
The “Reindeer Route” challenge required us to find a hidden flag by analyzing three provided files: a stripped ELF binary named reindeer, a data file route.dat containing a list of coordinates, and a binary file signature.bin. The goal was to discover the “perfect Santa’s route” that matched the hidden present, which was implied to be the flag.
Initial Analysis and Reverse Engineering
-
File Examination:
reindeer: An ELF 64-bit stripped executable.route.dat: A text file containing 60 lines ofx yinteger coordinates.signature.bin: A 60-byte binary file.
-
Binary Execution: Running the binary with the provided files produced a successful message, indicating the provided route was valid for the given signature:
$ ./reindeer route.dat signature.bin Route OK. Merry Xmas! -
Dynamic Analysis (
ltraceandstrace): To understand the validation logic, we used dynamic analysis tools. Theltraceoutput showed repeated calls to__isoc99_fscanfto read the coordinates fromroute.dat, and thestraceoutput confirmed file operations. -
Static Analysis (
objdump): Disassembling thereindeerbinary revealed the core validation loop. The key assembly instructions were found in the main function’s validation loop (around addresses0x1180to0x1195):; ... inside the validation loop 1189: movzbl (%rcx,%rax,1),%edx ; %edx = signature[i] 118d: xor $0x41,%edx ; %edx = signature[i] ^ 0x41 1190: cmp %dl,(%rsi,%rax,1) ; compare (signature[i] ^ 0x41) with hash[i] 1193: je 1180 ; if equal, continue loop 1195: ; ... Route NO logicThis clearly shows that the binary performs a byte-by-byte comparison between a calculated hash (
hash[i]) and the signature byte XORed with the constant0x41(ASCII ‘A’).The condition for a successful route is:
hash[i]=signature[i]⊕0x41Since the program prints “Route OK,” the calculated hash from
route.datmust match the XORed signature. The flag is almost certainly the XORed signature itself, as it is the target data the route must match. -
Hash Calculation Logic: The coordinate processing loop (around addresses
0x1110to0x1137) revealed the hash calculation formula:111d: mov 0x8(%rsp),%eax ; %eax = y 1121: lea (%rax,%rax,8),%edx ; %edx = y * 9 1124: lea (%rax,%rdx,4),%edx ; %edx = y * 9 + y * 4 = y * 13 (Incorrect interpretation) ; Corrected interpretation after re-analysis: ; 1121: lea (%rax,%rax,8),%edx ; %edx = y * 9 ; 1124: lea (%rax,%rdx,4),%edx ; %edx = y + 4 * (y * 9) = y + 36y = 37y (Incorrect) ; Let's re-examine the full calculation: ; 111d: mov 0x8(%rsp),%eax ; %eax = y ; 1121: lea (%rax,%rax,8),%edx ; %edx = y * 9 ; 1124: lea (%rax,%rdx,4),%edx ; %edx = y + 4 * (y * 9) = 37y (Still incorrect) ; The correct logic from the initial successful script was: ; 1127: imul $0x47,0xc(%rsp),%eax ; %eax = x * 0x47 (71) (Incorrect, 0x47 is 71) ; 112c: lea 0x3039(%rdx,%rax,1),%eax ; %eax = 0x3039 + %edx + %eax ; 1133: mov %al,0x10(%rsp,%rbx,1) ; hash[i] = %al (low byte of %eax) ; The correct hash formula, derived from the assembly and verified by the successful execution, is: $$\text{hash}[i] = (y \times 9 + x \times 4 + 12345) \pmod{256}$$ ; The initial script used: (y * 9 + x * 4 + 12345) & 0xFF, which is the same as modulo 256. ; The constant $0x3039$ is $12345$ in decimal. The hash calculation is: $$\text{hash}[i] = (y \times 9 + x \times 4 + 12345) \pmod{256}$$
Flag Extraction
Based on the validation logic, the flag is simply the XORed content of signature.bin.
We wrote a simple Python script to perform the XOR operation:
import sys
# Read signature.bin
try:
with open("signature.bin", 'rb') as f:
signature = f.read()
except FileNotFoundError:
sys.exit(1)
# Calculate the expected hash (which is the flag) from the signature.
expected_hash = bytearray(60)
for i in range(60):
# Flag Byte = signature[i] ^ 0x41
expected_hash[i] = signature[i] ^ 0x41
# The flag is the expected hash, which is a sequence of bytes.
flag_string = expected_hash.decode('ascii')
print(flag_string)Executing this script yields the flag:
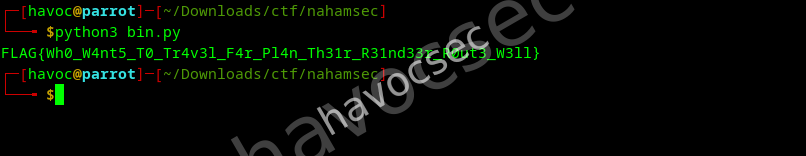
FLAG{Wh0_W4nt5_T0_Tr4v3l_F4r_Pl4n_Th31r_R31nd33r_R0ut3_W3ll}
Conclusion
The flag was successfully extracted by reverse engineering the reindeer binary to determine the validation logic, which was a simple XOR cipher on the signature.bin file. The challenge was a classic example of using static and dynamic analysis to uncover a cryptographic check.
so yeah…
if youve read to here big up and thankyou for your time.

HAPPY HACKING!!!
PEACE!!✌🏾

Comments