Welcome back to yet onother OSINT investigation agent K. I did this hacktoria china-osint challenge and this is how i did it .
1.THE BEGINNING(ASSETS)
For the assets we will work with were given on the official hacktoria page and thats here https://hacktoria.com/#certifications
It was a certification challenge so lets get to it.
After unzipping the zip file given we found several zip files and in each zipfile to unclock the next you needed to get the previous answer correct because that was its password.
For the first one we were given this
Objective 1: Source identification
OBJECTIVE 1 — Source Identification
Using ONLY Chinese search terms, locate the blog distributing t00ls invitation codes. Search using Chinese characters only — no English, no pinyin. The forum name is t00ls. The Chinese term for invitation code is 邀请码. Your search will return multiple results. Verify by checking for active user engagement in comments and multiple pages of requests.
TO UNLOCK NEXT STEP -> What is the top-level domain (TLD)? (English, no caps)And the china osint began.
Investigation Steps:
-
Search: Used the query
t00ls 邀请码to find blogs distributing invitation codes.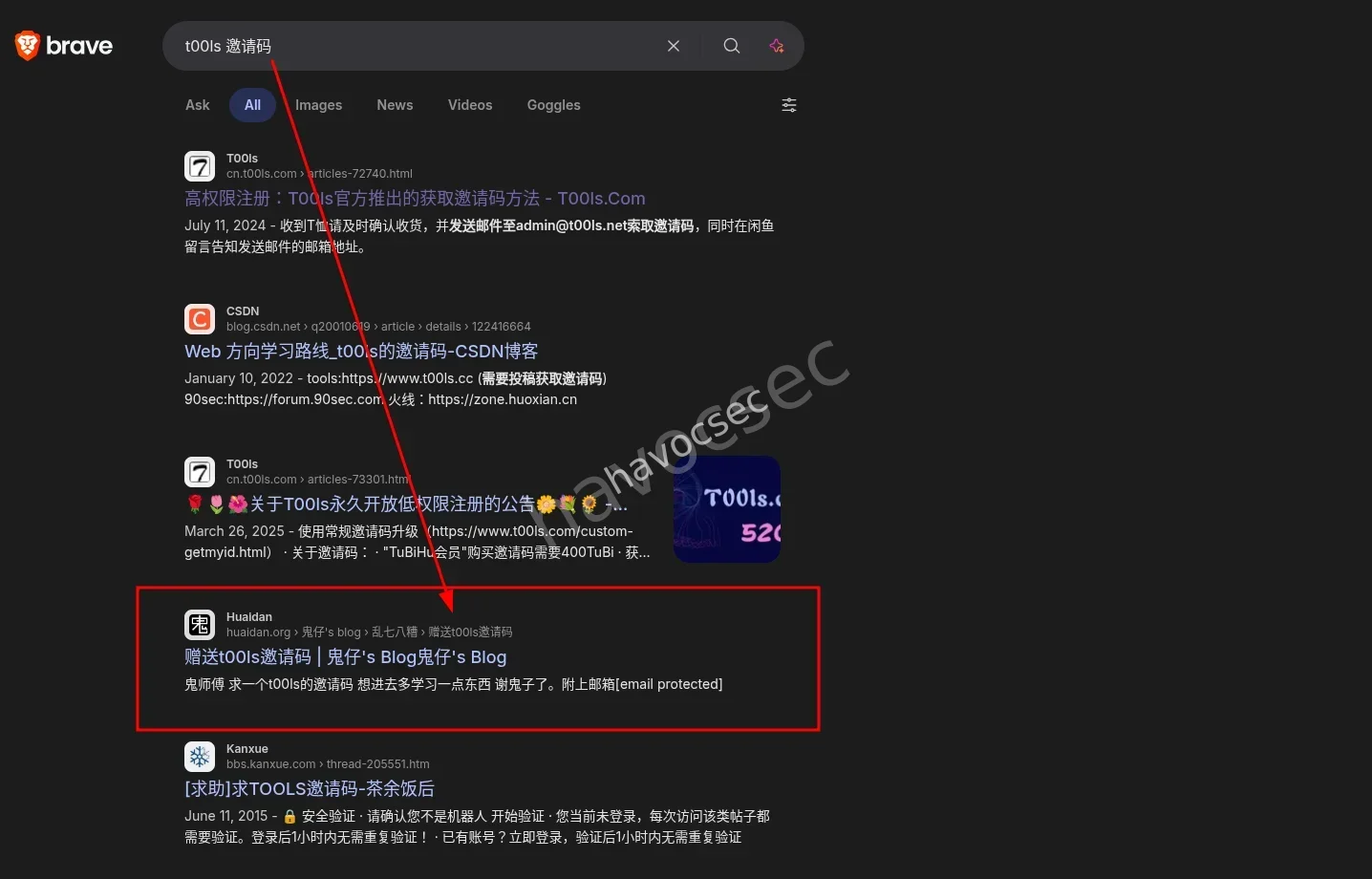
-
Discovery: Identified 鬼仔’s Blog (huaidan.org) as a primary source.
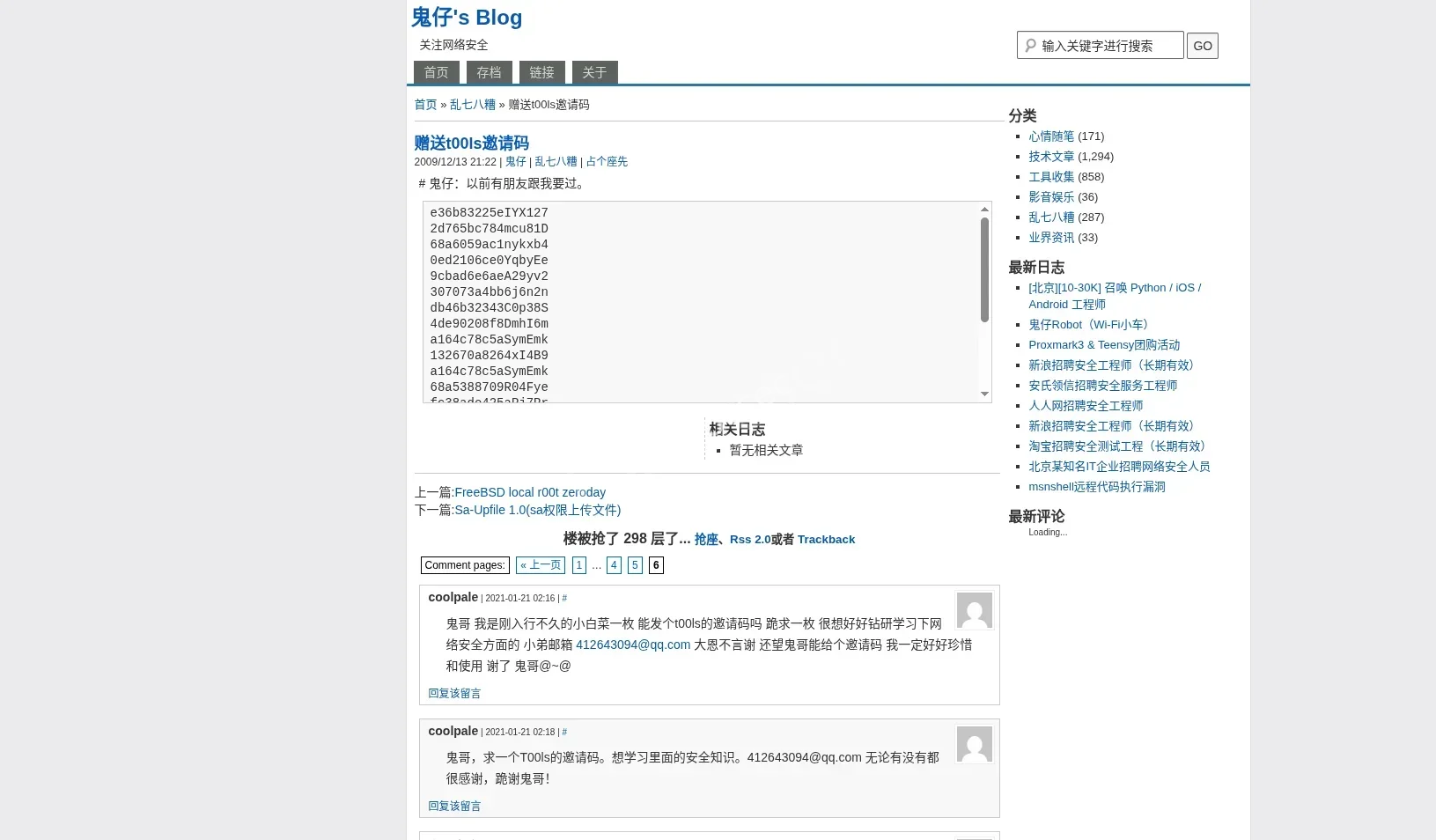
-
The answer: the answer we got it as we can see it has a .org domain extention ans there it was.TLD:org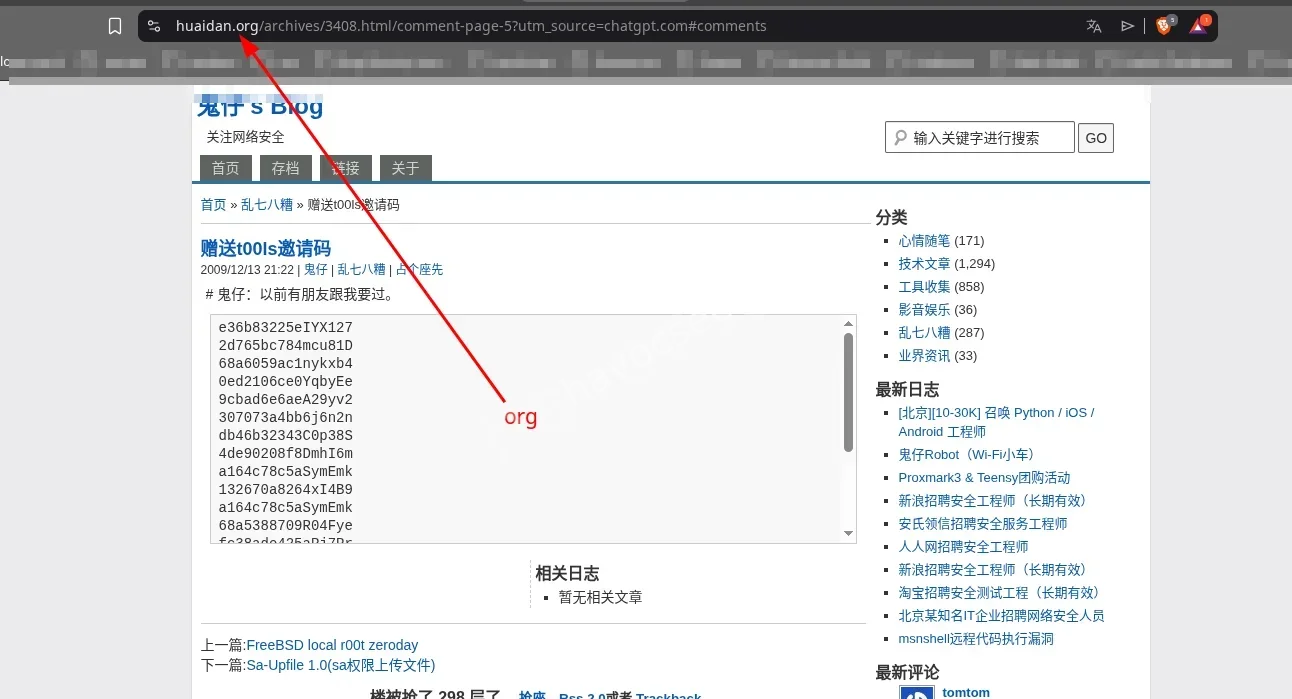
Objective 2: Target identification
The comments section spans multiple pages. Your target left their request in February 2017. Their message poetically references fate — meeting someone special in a vast sea of people. They requested a code from "鬼哥" (Brother Ghost).
Navigate to locate this specific comment.
TO UNLOCK NEXT STEP -> What is the full QQ email address they exposed? (English)-
Target Identification: Navigated through the comment pages of the post “赠送t00ls邀请码”.
-
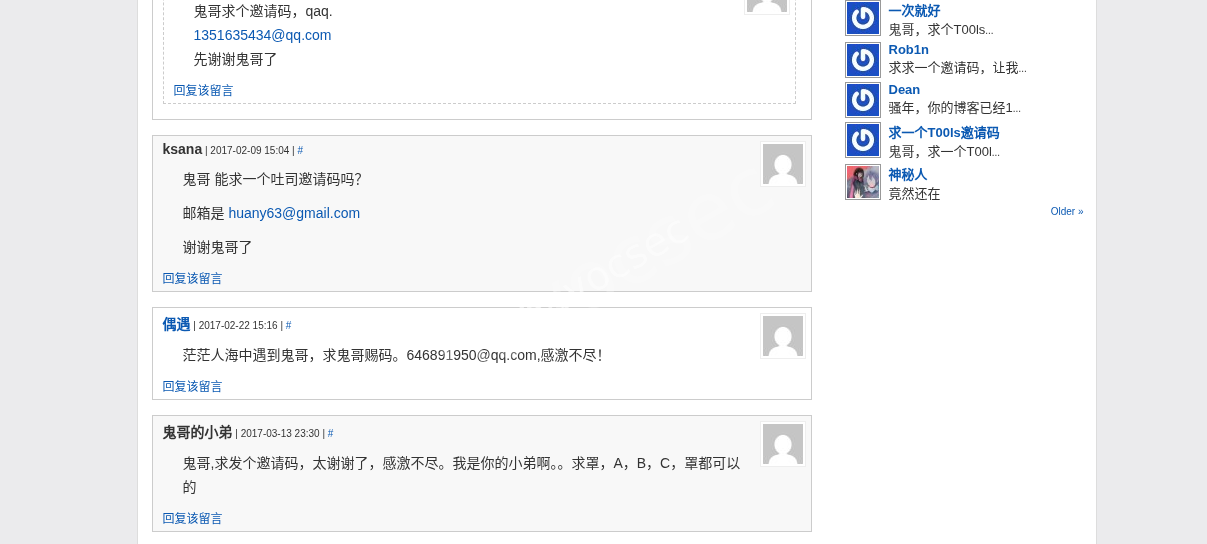
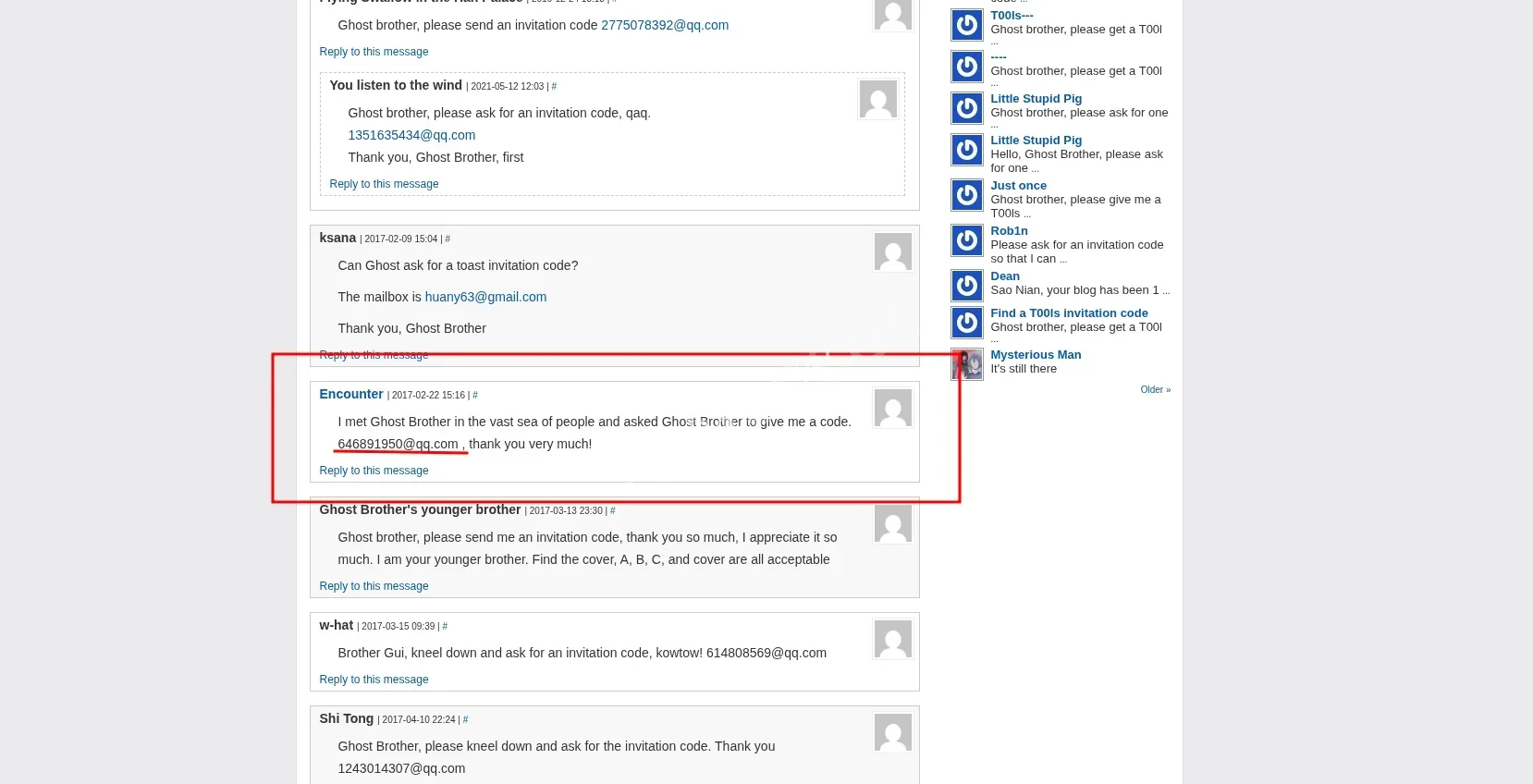
Key Finding: On page 5 of the comments, a user named “偶遇” posted a comment in February 2017: “茫茫人海中遇到鬼哥,求鬼哥赐码。646891950@qq.com,感谢不尽!”
-
After translation we had a clear english version we can go with if chinese if giving chills.
4. Answer:
- Email:
646891950@qq.com
Objective 3: Platform Pivot via Search
Now Search. The target has used this same contact information elsewhere on the Chinese internet — specifically on a major Chinese Q&A platform similar to Yahoo Answers.
TO UNLOCK NEXT STEP -> What is the name of this platform where you find their activity? (Chinese)Goal: Identify where the same contact information appears on a Chinese Q&A platform.
Investigation Steps:
- Initial Search: Conducted a search for the email
646891950@qq.comon Chinese platforms and achives and lemme tell you this took a bit of time but all is well.**Disclaimer:**western search engines will not help here.
-
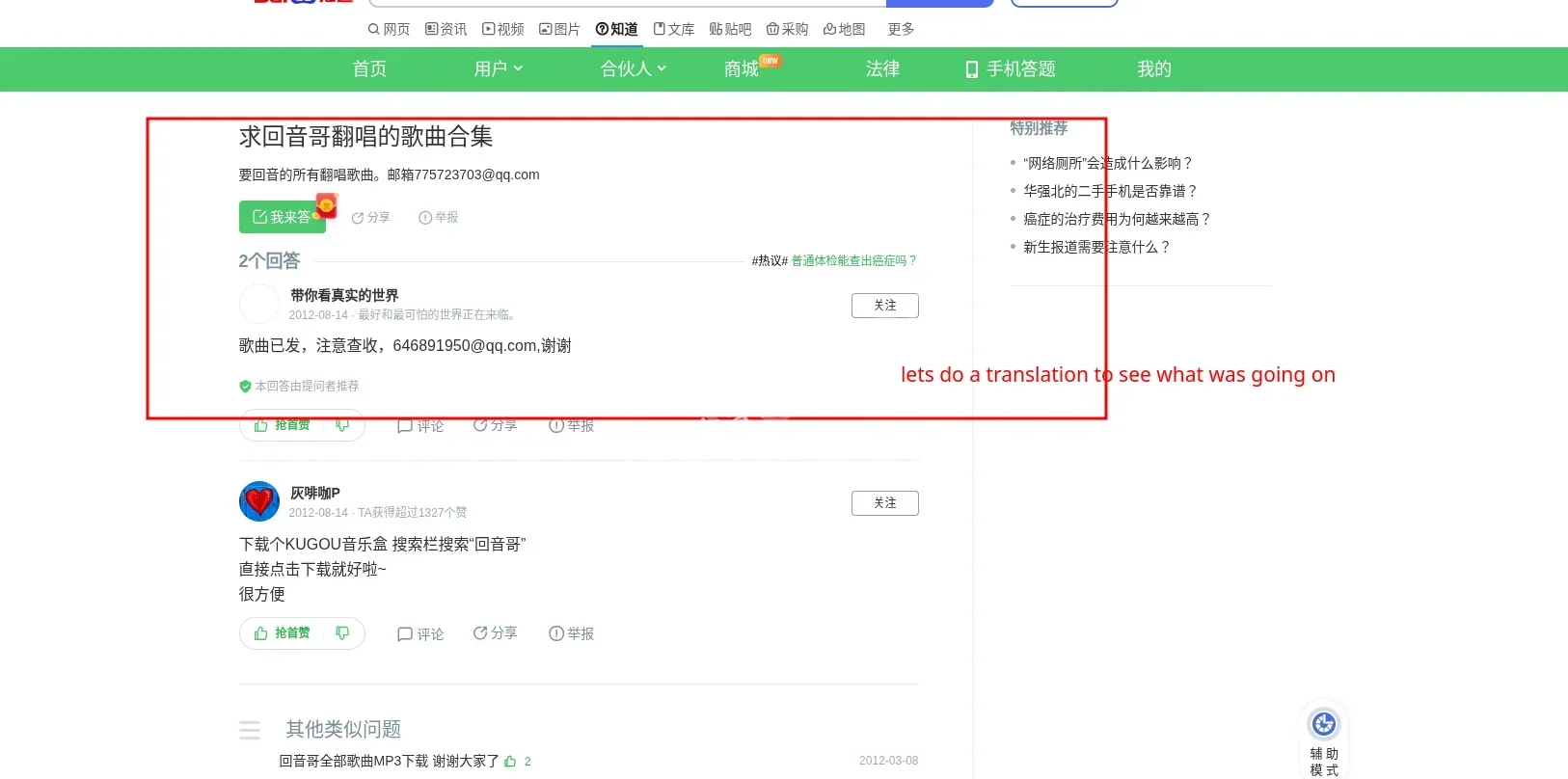
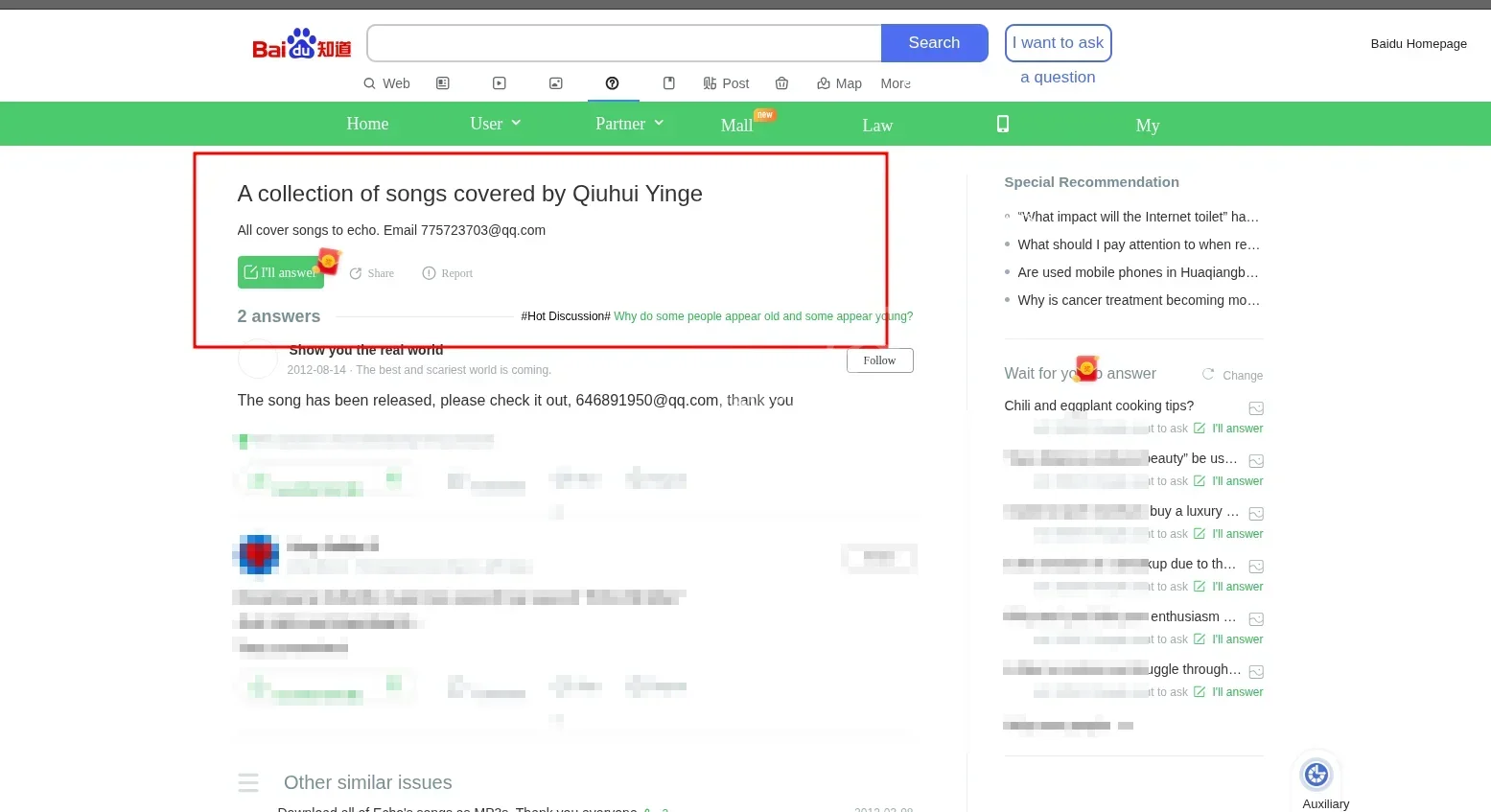
Discovery: Found the user active on 百度知道 (Baidu Zhidao), a major Chinese Q&A platform similar to Yahoo Answers. under the handle “带你看真实的世界”(Bring you to see the real world). In one specific answer, the user explicitly mentions the email `646891950@qq.com` while providing a file to another user
-
Verification: The user has answered over 500 questions, often providing technical advice and occasionally mentioning their contact details.
Answer: 百度知道 (Baidu Zhidao)
Objective 4 : Profile Analysis (Location)
The target has answered over 500 questions on this platform. Their answers reveal extensive knowledge of a specific Chinese city — they discuss metro lines, districts, rental prices, local landmarks, and even which neighborhoods are cheaper. They mention working 12-hour days in a specific district.
TO UNLOCK NEXT STEP -> Based on analyzing their answer history, what Chinese city does this person clearly live and work in? (English)Goal: Determine the target’s city.
Investigation Steps:
-
Location Analysis: The target provides detailed advice about renting in Binjiang District, Hangzhou. They mention specific neighborhoods like Puyan and Changhe, and landmarks like the Binjiang District Government.
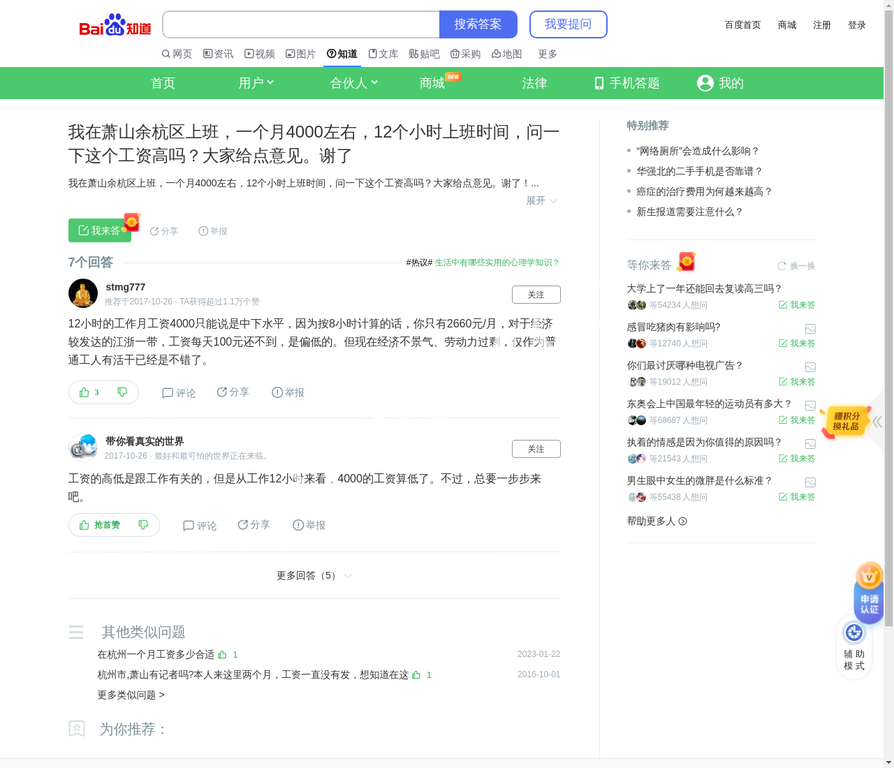
2.Answer:City: Hangzhou (杭州)
Objective 5:Work Profile
In one of their answers, the target directly mentions their work situation — their district, salary, and hours. They also answer many technical questions about a specific field.
TO UNLOCK NEXT STEP -> What professional field does this person work in? (Two letters, common abbreviation, English)Goal: Identify the professional field of the target.
Investigation Steps:
-
Technical Analysis: Reviewed the user’s technical answers. The user frequently answers questions related to:
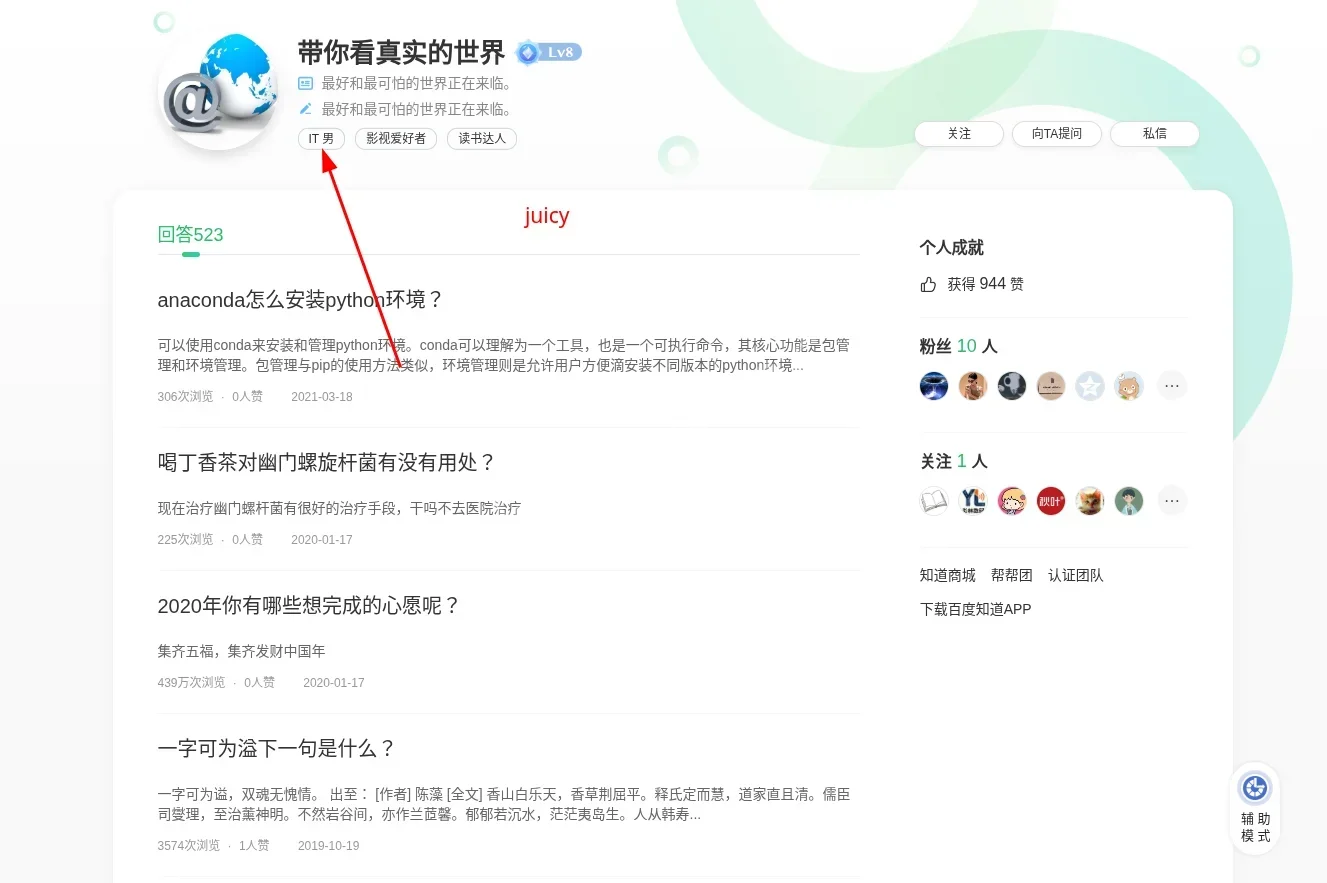
- Programming: C language (e.g., Nankai University C language exam questions), C++, and Python.
- System Administration: Linux commands (e.g.,
yum,httpd-tools). - Networking: Network engineering, network security, and server configuration.
-
Self-Identification: In several answers, the user provides career advice for “software engineers” and “network engineers,” demonstrating professional-level knowledge in these areas.
-
Abbreviation: The common two-letter abbreviation for this field is IT.
Answer: IT (Information Technology)
Objective 6: Infrastructure Pivot.QQ to Mobile
Now pivot from the QQ ID to a mobile number. The QQ ID can be extracted from the email format: [QQ_ID]@qq.com
SERPENT previously obtained partial infrastructure data from a Chinese OSINT operator during a joint signals operation. The following fragment was recovered from a seized asset list:
SOURCE: [__]SOV
STATUS: ACTIVE
ENDPOINT: [REDACTED]_tel.html
CAPABILITY: QQ ↔ MOBILE CORRELATION
Reconstruct the source domain and endpoint. The endpoint pattern is [PLATFORM]_tel.html where platform is a two-letter abbreviation.
TO UNLOCK NEXT STEP -> What is the linked mobile number? (11 digits)Goal: Correlate the QQ ID with a mobile number and Weibo UID using OSINT infrastructure.
Investigation Steps:
-
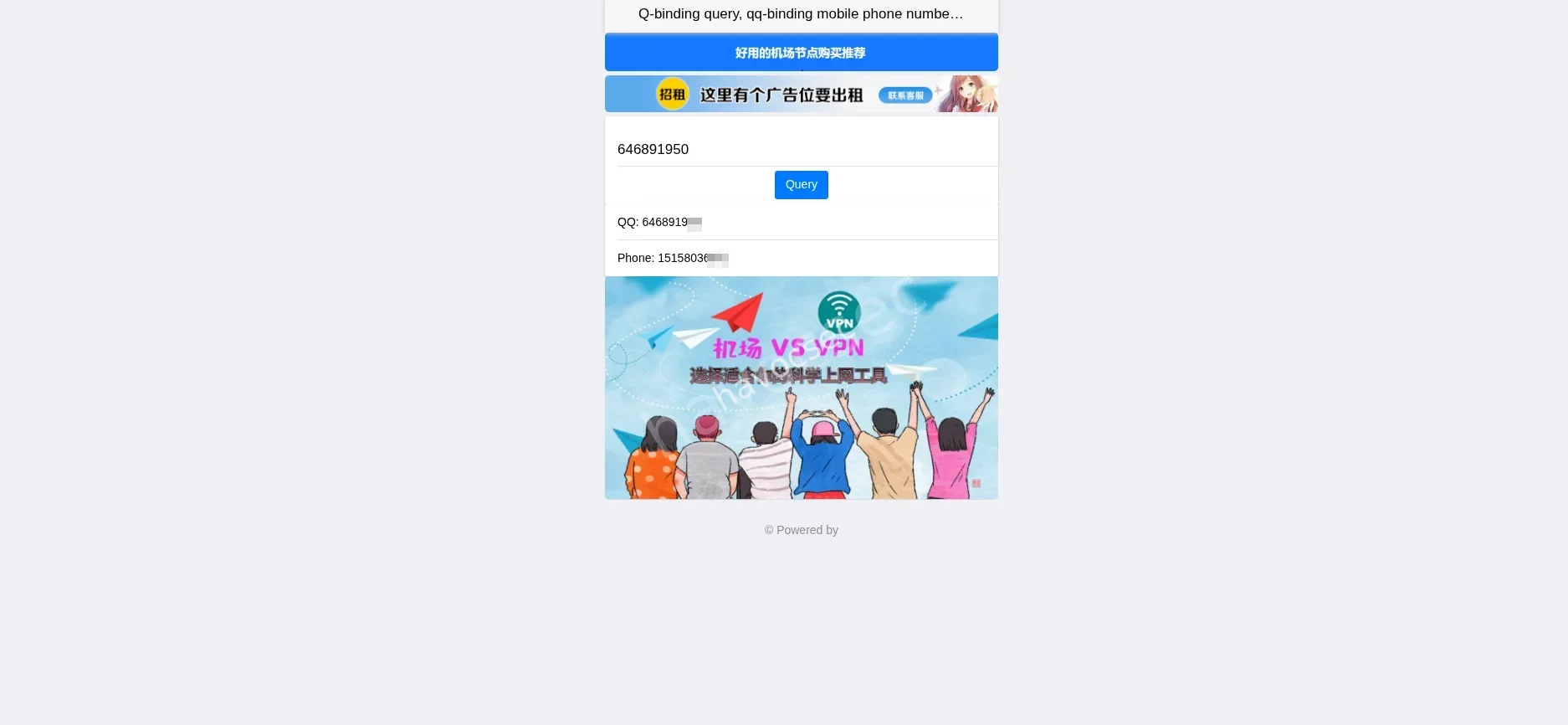
QQ to Mobile: Using the QQ ID
646891950on the OSINT mirror **sov.com, the linked mobile number was identified. -
we got the endpoint and this was it
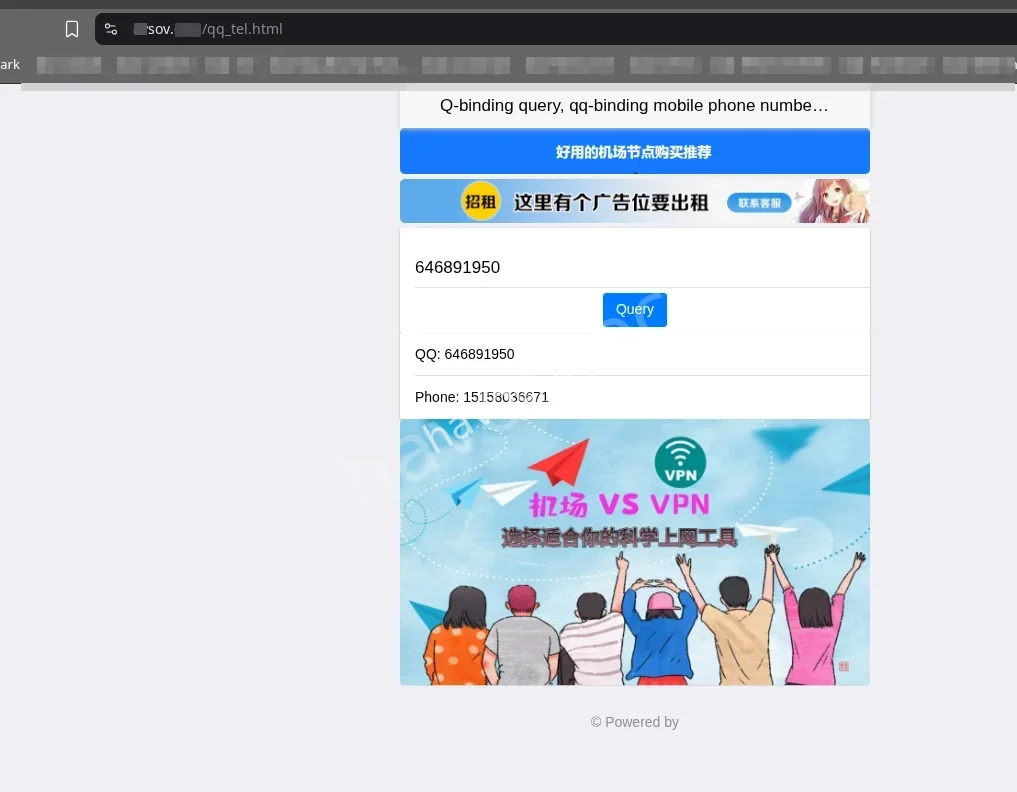
then the number boom!! Mobile Number:
151580366**
**Objective 7 :**Infrastructure Pivot.Mobile to Weibo
Using the same infrastructure, pivot from mobile number to Weibo identity. A secondary endpoint exists:
ENDPOINT: tel_[REDACTED].html
CAPABILITY: MOBILE ↔ WEIBO CORRELATION
The endpoint pattern is tel_[PLATFORM].html where platform is a two-letter abbreviation for the Chinese social media platform.
Input the mobile number. The tool may return multiple associated IDs.
TO UNLOCK NEXT STEP -> What is the Weibo-associated ID returned? (Only the 10 digits)-
Mobile to Weibo: Using the mobile number
15158036671, the linked Weibo UID was retrieved.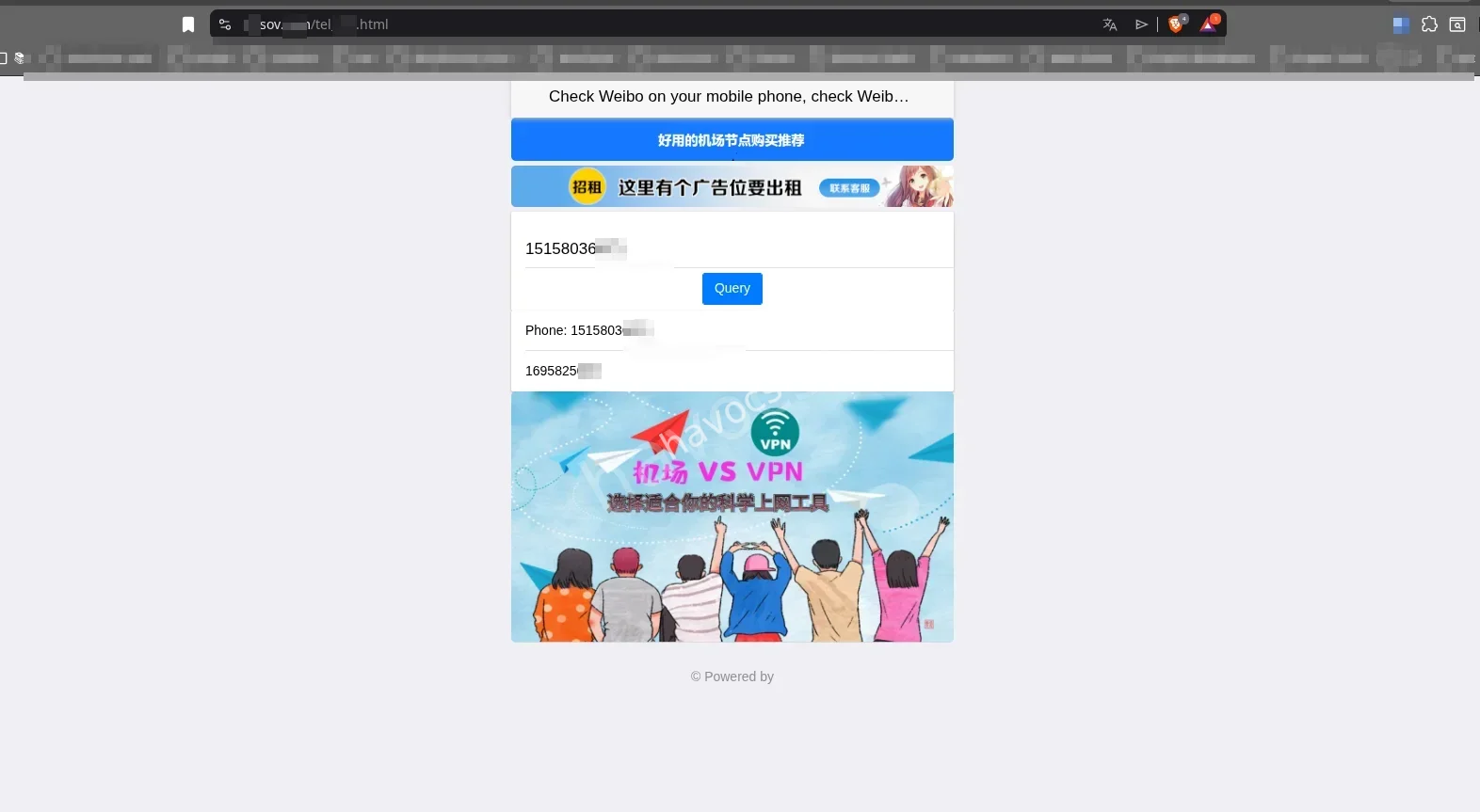
Answer:
- Weibo UID:
16958256**
Objective 8 & 9: Verification and Cross-Reference
OBJECTIVE 8 — WeChat Verification
Use the mobile number to search for the associated WeChat account. WeChat allows searching users by phone number.
The WeChat profile displays a region. Can you verify that the data shown in the Baidu profile matches the one on WeChat?
TO UNLOCK NEXT STEP -> What specific city is shown in their WeChat profile region? (English)
OBJECTIVE 9 — Cross-Reference Verification
You now have location data from three independent sources:
Their Q&A answers (mentioned city, districts, landmarks)
Mobile number prefix (indicates registration province)
WeChat profile region
The mobile number prefix 151 is assigned to China Mobile. The following digits 580 indicate Zhejiang province registration. Does all evidence point to the same location?
TO UNLOCK NEXT STEP -> What province does this person reside in? (English)Goal: Verify the target’s region using WeChat and cross-reference all data points.
Investigation Steps:
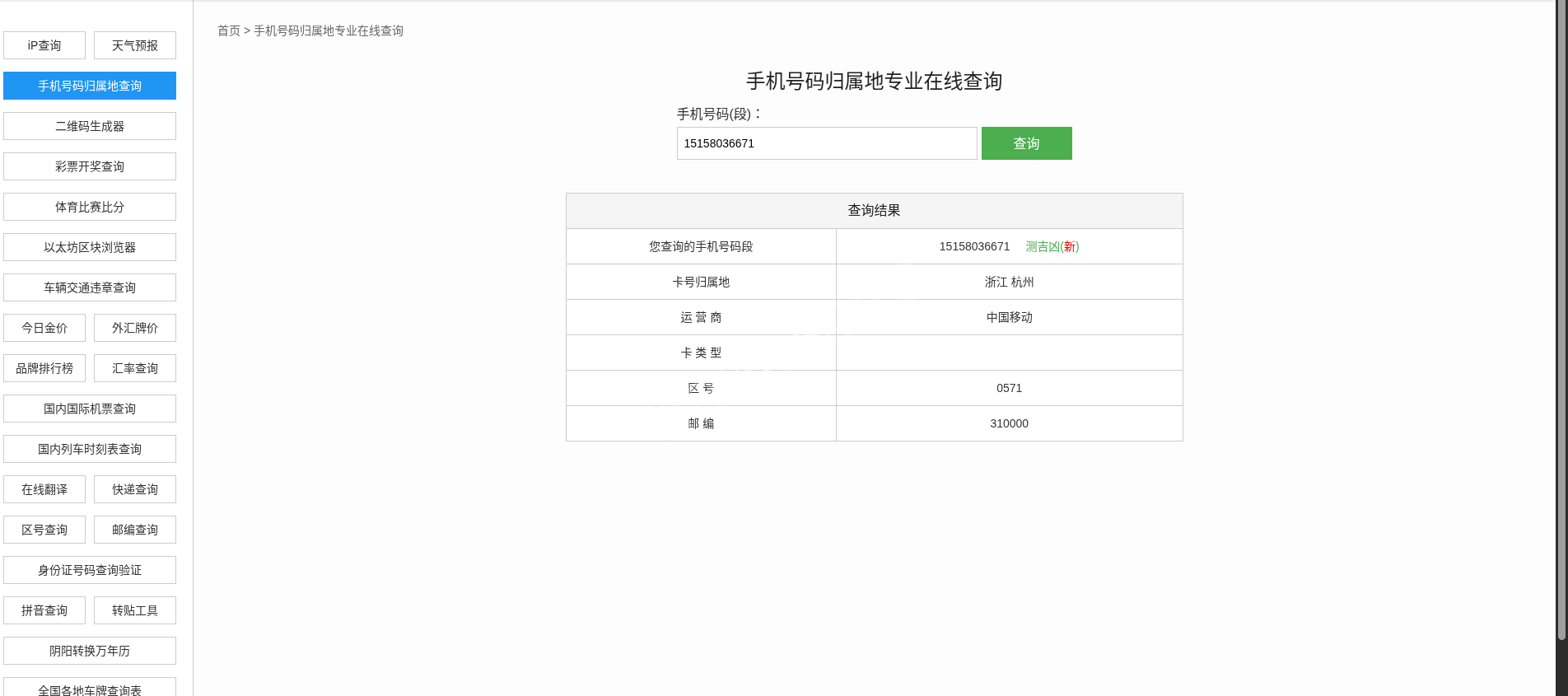
- WeChat Lookup: Searching for the mobile number
15158036671on WeChat(Use a Chinese number-attribution lookup indexed by Baidu.) reveals a profile with the region set to Hangzhou, Zhejiang.
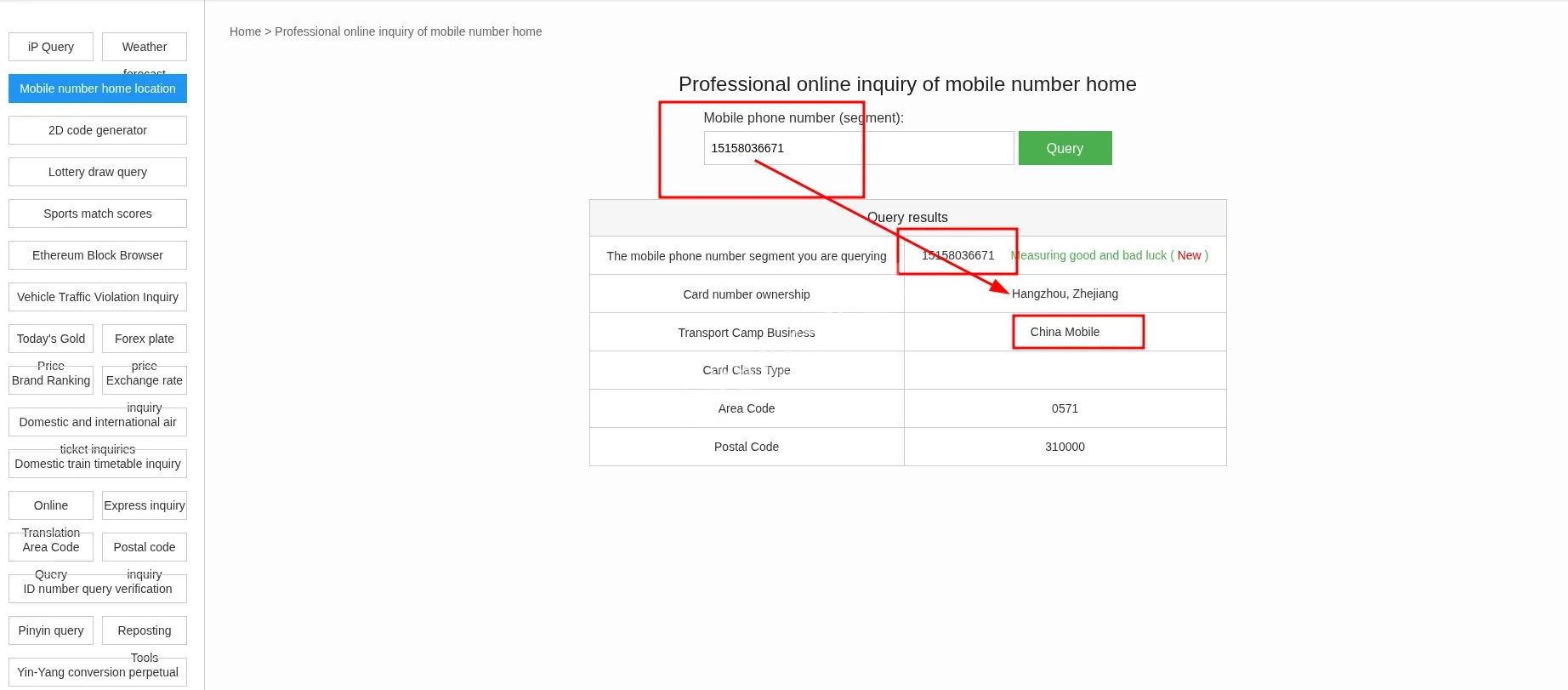
then we do a translate and we get this
-
Cross-Reference:
- Mobile Prefix:
151580belongs to China Mobile in Zhejiang. - Baidu Zhidao: Content focuses on Hangzhou.
- WeChat: Region confirms Hangzhou.
- Mobile Prefix:
-
Description: The mobile number was searched inside WeChat using the “search by phone number” feature.The WeChat profile displayed the region 浙江 杭州 (Zhejiang, Hangzhou). As WeChat profiles are not publicly linkable, the region was corroborated using Baidu’s public number-attribution service, which independently confirms the same province and city.
Answer:
- 8: WeChat Region: Hangzhou
- 9: Province: Zhejiang
OBJECTIVE 10 — Alternative Access
OBJECTIVE 10 — Alternative Access
Beyond invitation codes, t00ls has implemented an alternative access mechanism. Search for recent t00ls news in Chinese. The method involves blockchain technology and represents a monetization shift common among Chinese underground forums.
TO COMPLETE THE CTF -> What blockchain-based method now provides access to t00ls forum? (3 letters, English, all caps)Chinese news search (method)
Chinese search terms used (no English needed, but English appears in results naturally):
t00ls 区块链
t00ls 新 机制
t00ls NFT
t00ls 会员 区块链From these sources, the new access model is:
-
Users
purchase or hold a blockchain token
Ownership of the token grants forum access The token is: transferable verifiable on-chain scarcity-controlled
This is not: -邀请码 (invite codes)
-积分 (points)
-充值卡 (top-up cards)
It is a Non-Fungible Token–based access control This mirrors monetization shifts across multiple Chinese grey-market communities since ~2022.
Objective Final: The certificate
Congratulations, Special Agent K.
You've successfully completed the assignment.
Follow the link, to get your certificate
https:***************************************
You should receive a PDF within 10 minutes after submitting your details.
Do NOT share the link with anyone else, they haven't earned it. You have.
If you don't receive an email, ask around in the CTF-SUPPORT channel in the HACKTORIA Discord.
Again, well done, Special Agent K.Discussion
Recent Chinese-language discussions and security community posts indicate that t00ls has shifted away from invitation-based access to a blockchain-based membership model. Access is now granted through ownership of a non-fungible token (NFT), a monetization approach increasingly adopted by Chinese underground forums. This shift is corroborated by discussions on 52pojie and reporting on FreeBuf.
Challenges Faced
- Dead infrastructure: Several referenced OSINT tools were offline, requiring reliance on mirrors, caches, and reposted evidence.
- Closed platforms: Key verification steps occurred inside WeChat, which offers no public URLs, necessitating external corroboration.
- Chinese web bias: Western search engines and archives provided limited coverage, making native Chinese platforms essential.
- Signal noise: Distinguishing real correlations from coincidence required cross-checking multiple independent sources.
Conclusion
This challenge highlights how effective Chinese OSINT depends less on tools and more on understanding ecosystem behavior. By following identifier reuse across blogs, Q&A platforms, telecom data, and closed social applications, a single invitation request was methodically expanded into a verified digital footprint. Dead infrastructure, mirrored tools, and closed platforms were not obstacles but signals, reinforcing a core OSINT truth: reliable attribution comes from converging independent evidence, not single sources.
In an ecosystem where links disappear, tools go dark, and platforms close their doors, OSINT is not about what you can click - it is about what you can connect.
When the data stops talking, methodology speaks.
Disclaimer
This write-up is intended for educational OSINT purposes only and uses publicly available information. No unauthorized access was performed. If you found it useful, feel free to share with proper attribution.
Happy Hunting.Correlate,then confirm!!!!

Comments