The year is wrapping up. The eggnog is flowing, the lights are twinkling, and the world’s security teams are collectively taking a deep, exhausted breath. But as a developer, a security engineer, or a seasoned CTF player, you know the truth: the holidays are just a brief, vulnerable lull before the next wave of chaos. The threat actors aren’t taking a break; they’re just compiling their Naughty List for 2026.
As someone who’s seen a millennium of exploits—from ancient buffer overflows to the latest zero-days—I’m here to tell you what’s coming. Forget the gifts under the tree; these are the threats you need to unwrap and neutralize before the New Year’s ball drops.
Prediction 1: The AI Avalanche – The Gift That Keeps on Hacking
If 2025 was the year Generative AI became a tool for developers, 2026 will be the year it becomes the ultimate weapon for attackers. This isn’t about simple phishing emails anymore; this is about scale and sophistication.
The Threat:
- Automated Malware Generation: AI will lower the barrier to entry for complex malware. Attackers will use LLMs to rapidly generate polymorphic code, test exploit chains, and bypass traditional signature-based defenses at machine speed.

- Deepfake Social Engineering: Imagine a deepfake video call from your CEO, or a perfectly crafted voice message from a colleague, complete with their usual verbal tics. AI-driven identity deception will make traditional MFA and human vigilance insufficient.

- Shadow AI: The biggest risk will be the unmanaged, unvetted AI agents and tools developers and employees bring into the corporate environment. These “Shadow AI” instances will become the new, unmonitored insider threat vector, leaking sensitive code and data.
The Survival Guide: You need AI to fight AI. Invest heavily in AI-powered threat detection that can analyze behavioral anomalies, not just signatures. For developers, this means rigorous prompt injection testing on any LLM-integrated application.
Prediction 2: The Quantum Countdown – The Unbreakable Code is Breaking
The threat of quantum computing has always felt like a distant, theoretical problem. In 2026, it moves from the realm of science fiction to the top of the CISO’s agenda. The danger isn’t that a quantum computer will be ready to crack RSA next year, but that attackers are already performing “Harvest Now, Decrypt Later” attacks.
The Threat:
- Attackers are stockpiling encrypted data today, knowing that when a fault-tolerant quantum computer arrives, they can decrypt the entire haul instantly.
- The transition to Post-Quantum Cryptography (PQC) is slow, complex, and fraught with implementation errors. Organizations that haven’t started inventorying their cryptographic assets and planning their PQC migration will be critically exposed.
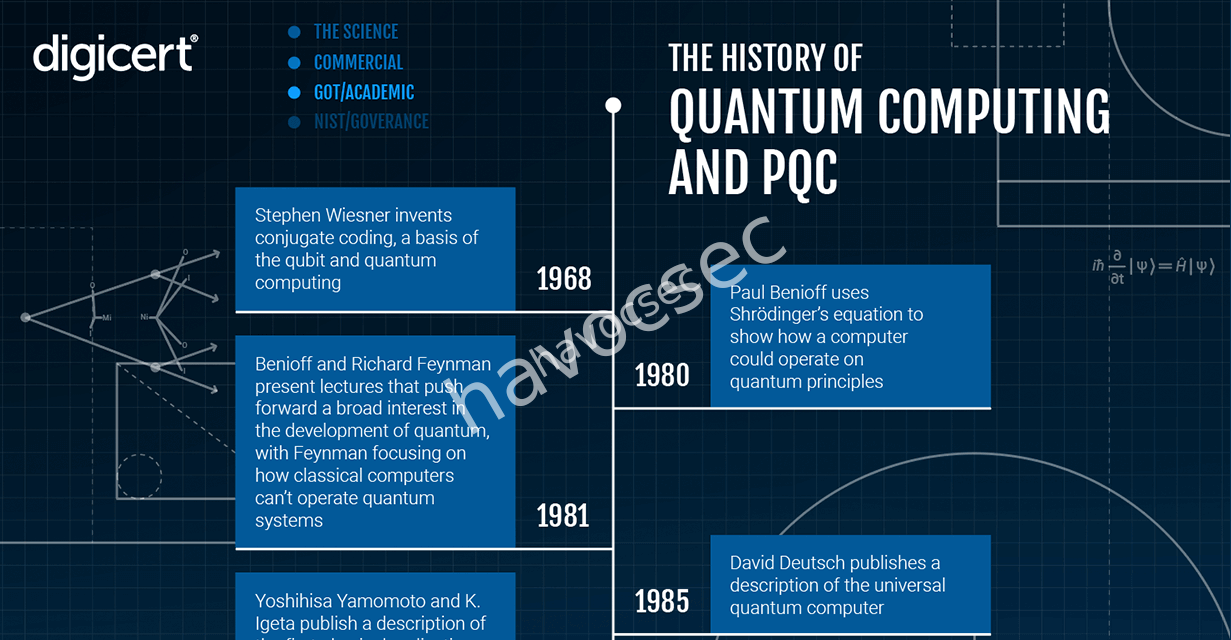
The Survival Guide: Start your crypto-agility journey now. Inventory every certificate, every key, and every protocol. Developers must begin experimenting with PQC algorithms like CRYSTALS-Kyber and CRYSTALS-Dilithium. This is a multi-year project, and 2026 is the year the clock runs out on procrastination.
Prediction 3: DevSecOps: Shift Left or Get Left Behind (The Developer’s New Year’s Resolution)
For too long, security has been the grumpy gatekeeper at the end of the CI/CD pipeline. In 2026, that model is dead. The sheer volume and velocity of code being generated—often with the help of AI assistants—means security must be baked in from the first commit.
The Threat:
- Supply Chain Attacks: The dependency hell is getting worse. Attackers will continue to poison open-source repositories, targeting the weakest link in the software supply chain.
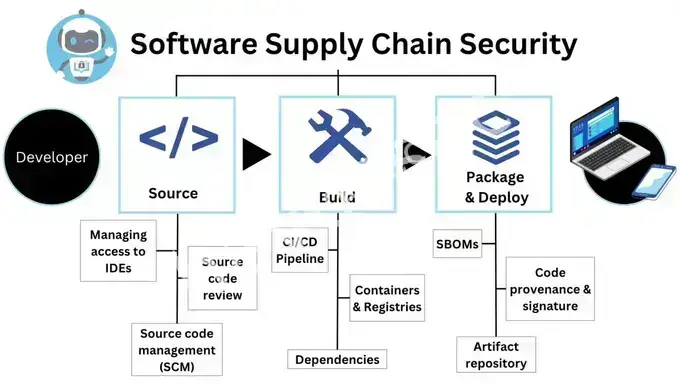
- Misconfigured Infrastructure-as-Code (IaC): As teams rely more on IaC (Terraform, CloudFormation), a single misconfiguration in a template can expose an entire cloud environment.
The Survival Guide: Shift Left is no longer a buzzword; it’s a mandate. Implement Software Composition Analysis (SCA) and Static Application Security Testing (SAST) directly into the IDE and the pull request process. Treat security vulnerabilities like build failures. For IaC, adopt Policy-as-Code tools to enforce security standards before deployment even begins.
Prediction 4: Zero Trust, Zero Excuses (The Only Firewall Santa Needs)
The perimeter is gone. The network is the internet. The user is the threat. The only sane response is the full, uncompromising adoption of Zero Trust Architecture (ZTA).
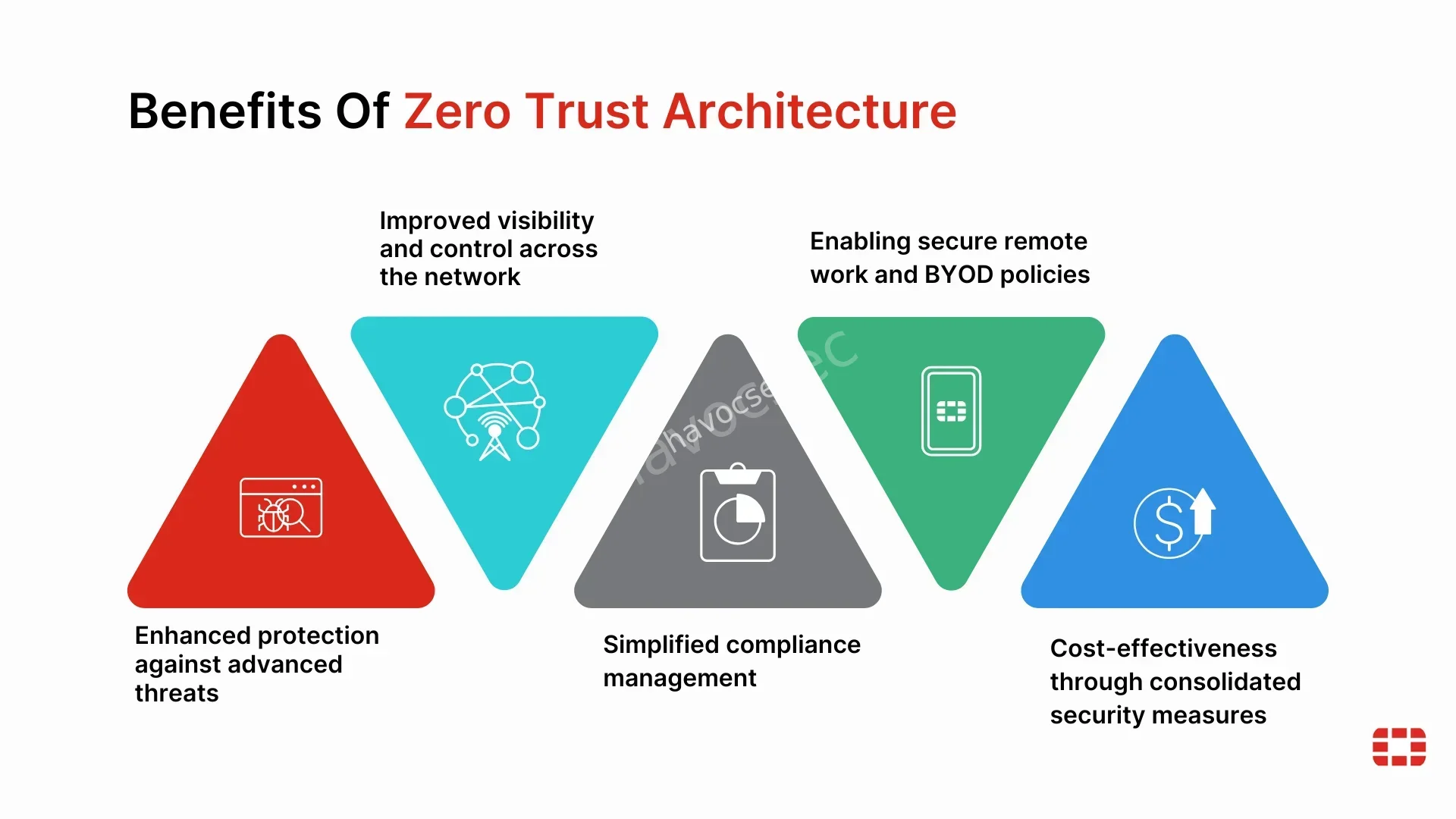
The Threat:
- Lateral movement within compromised networks remains the primary way attackers turn a small breach into a catastrophic event.
- Legacy VPNs and flat networks are the gift that keeps on giving to attackers.
The Survival Guide: Stop trusting anything. Every user, every device, and every application must be authenticated and authorized for every single access request. Focus on micro-segmentation and continuous verification. For developers, this means designing applications with ZTA principles in mind, ensuring every API call is properly authorized, regardless of its origin.
Conclusion: Secure Your Sleigh, HavocSec
The holiday season is a time for reflection, but in our world, it’s a time for preparation. The threats of 2026—driven by AI, accelerated by quantum fears, and amplified by complex supply chains—demand a proactive, developer-centric security posture.
Don’t let your code end up on the Naughty List. Secure your sleigh, check your dependencies twice, and make Shift Left your ultimate New Year’s resolution.
From all of us at HavocSec, have a secure and happy New Year!

HAPPY HACKING!!🎄

Comments