I had the opportunity to participate in this year’s SWIMMER OSINT CTF as part of team B3a1th, and it was a genuinely enjoyable and educational experience.This writeup is my attempt to document how I approached some of the challenges. I am still learning how to properly structure CTF writeups, so the explanations and language may not be perfect. That said, I hope walking through my thought process and steps taken can still be useful to others who are learning as well.
With that out of the way, let’s get into it. .
For the challenges i solved a few of them,thanks to my teammate big up Mr sapien you did good, hope we can do more in the future..
Getting started
1.rain_01_social
for this there were some clues given one being rain had a x account so after seeing the given screenshot,i saw something worth looking and thats the comment under the blocked user because everything else in the image would take sometime so afyer copying the comment i used the x search functionality and it yielded .
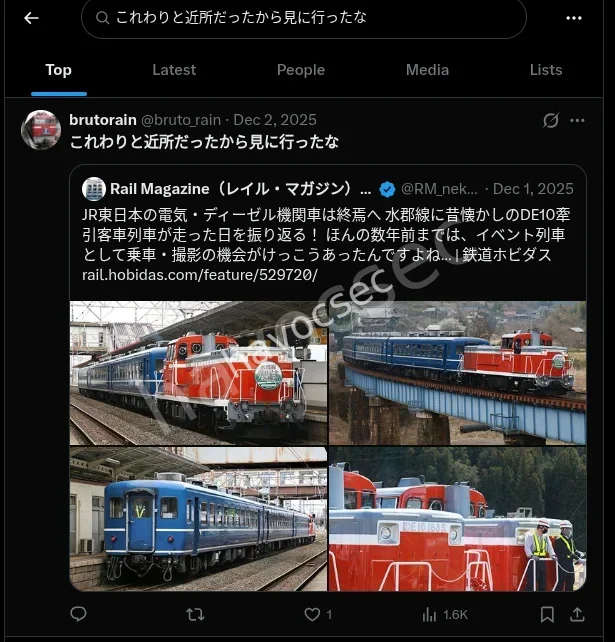
as you can see the account name clear now.
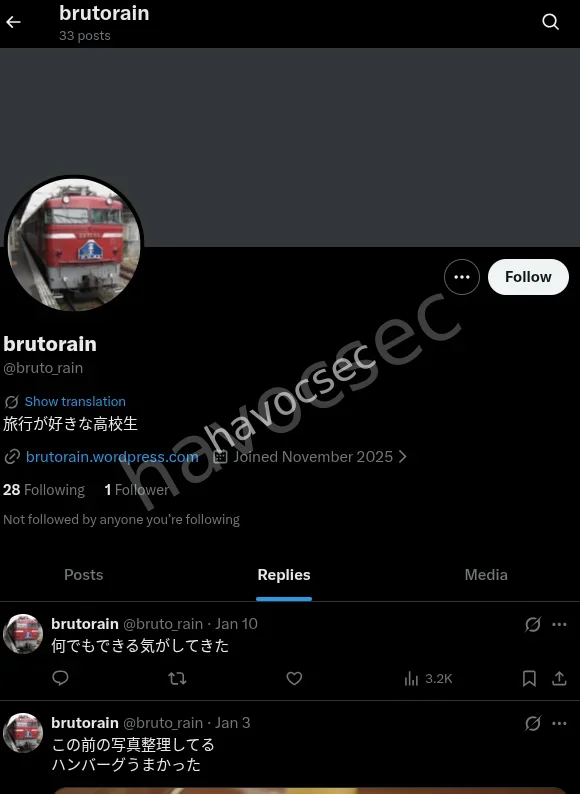
and there we had our flag
SWIMMER{@bruto_rain}
to the next one;
rain_06_ai
for this the description was pretty simple
to Identify the AI tool used to create the Tokyo Station image on rain’s blog https://brutorain.wordpress.com/
Initial Reconnaissance
I started by visiting the provided blog URL to locate the image of Tokyo Station.
Action: Navigated to https://brutorain.wordpress.com/.
Observation: The blog has several posts. I checked the post titled “日常を記録する” (Recording daily life), dated January 3, 2026.
2. Locating the Target Image
Inside the post “日常を記録する”, I found a realistic image of Tokyo Station.
Command used to find image URLs:
// Executed in browser console
Array.from(document.querySelectorAll('img')).map(img => img.src)Output:
[
"https://brutorain.wordpress.com/wp-content/uploads/2026/01/tokyo_0003.jpeg?w=1024",
...
]3. Image Acquisition and Metadata Analysis
I downloaded the image directly to my machine to perform a deep inspection of its metadata, as AI tools often leave “fingerprints” in the EXIF data.

Command:
import requests
from PIL import Image
from PIL.ExifTags import TAGS
url = 'https://brutorain.wordpress.com/wp-content/uploads/2026/01/tokyo_0003.jpeg'
response = requests.get(url, stream=True)
with open('tokyo.jpg', 'wb') as f:
for chunk in response.iter_content(chunk_size=8192):
f.write(chunk)
img = Image.open('tokyo.jpg')
exif_data = img._getexif()
if exif_data:
for tag, value in exif_data.items():
tag_name = TAGS.get(tag, tag)
print(f'{tag_name}: {value}')4. Discovery of AI Metadata
The metadata analysis revealed a highly specific UserComment field containing a JSON object.
Extracted Metadata Snippet:
{
"aigc_info": {
"aigc_label_type": 0,
"source_info": "dreamina"
},
"data": {
"os": "web",
"product": "dreamina",
"exportType": "generation",
"pictureId": "0"
},
"trace_info": {
"originItemId": "7590949739743448328"
}
}5. Tool Identification
The metadata explicitly mentions “dreamina” as the source_info and product.
Research:
- Dreamina is an AI creative platform developed by ByteDance (the creators of TikTok and CapCut).
- It is used for generating high-quality AI images and videos.
Final Conclusion
The image was generated using the AI tool Dreamina. so the flag for this wass SWIMMER{dreamina}
To the next one.
debeyohiru_01_social
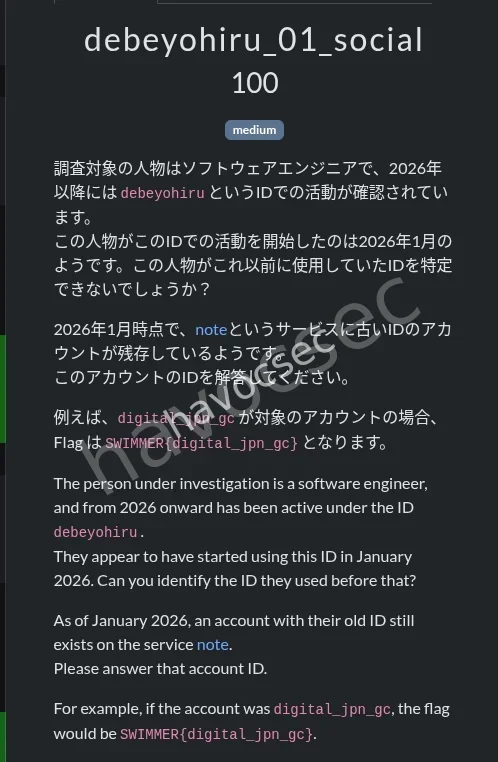
for this challenge we had to look for an account with the id debeyohiru online.so we use sherlock or any other easy on your part but unfortunately lets get to it directly
I did my fast research and got a hit and it was on bluesky and here it is
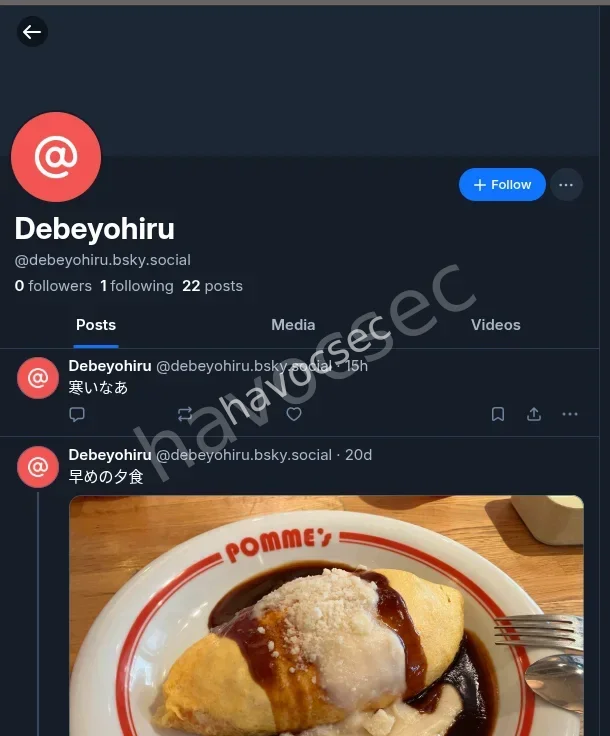
so i browsed and had a hit on the account on note.com there wqs this screenshot he posted,so on the url i saw the username .
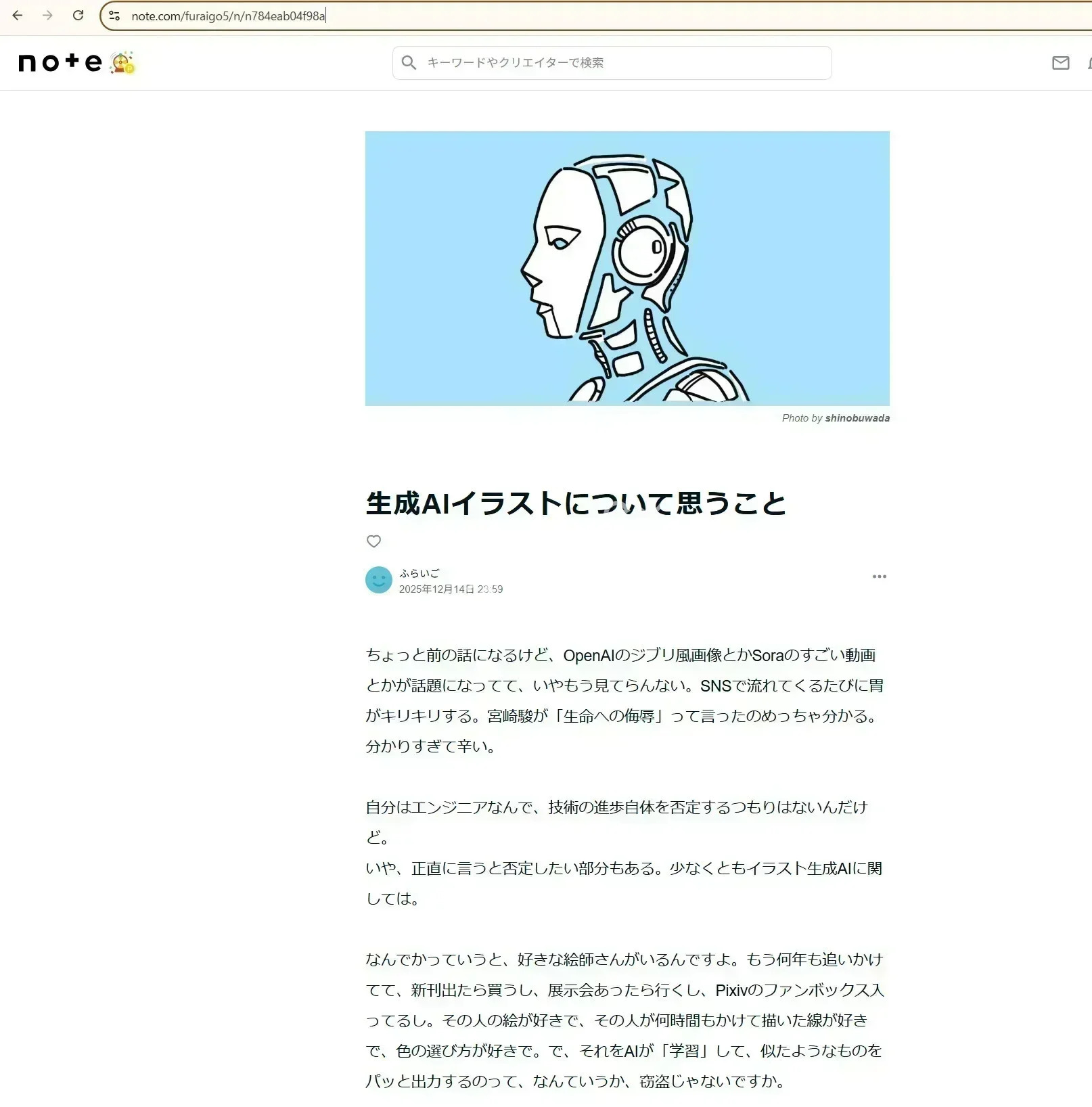
so i confirmed you know what i mean and this was it
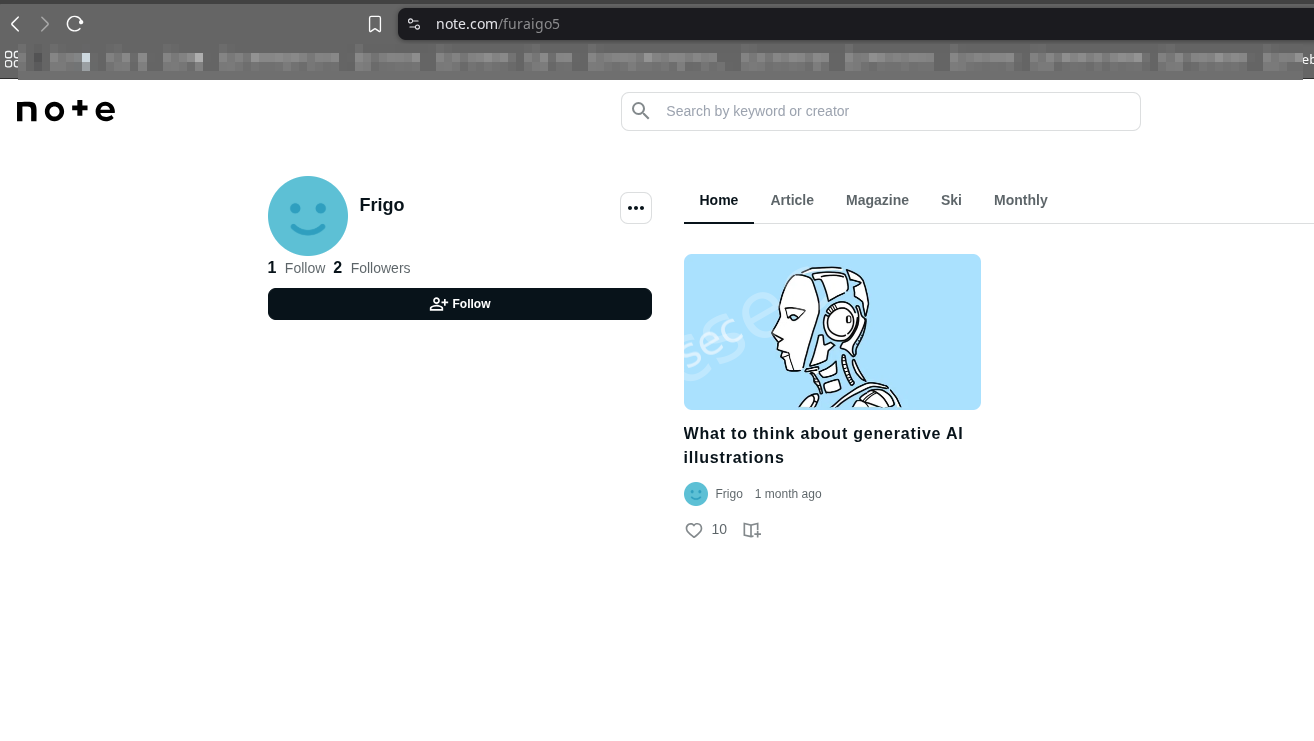
and there we had our flag SWIMMER{furaigo5}
to the next now..
debeyohiru_02_profile
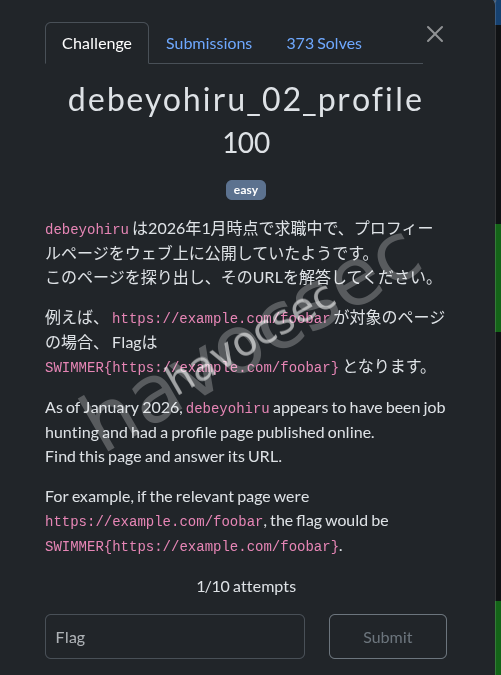
i did alot of search for this but while procastinating an hint was released on discord and then boom i had it
it was a github we had to look and see and this was it
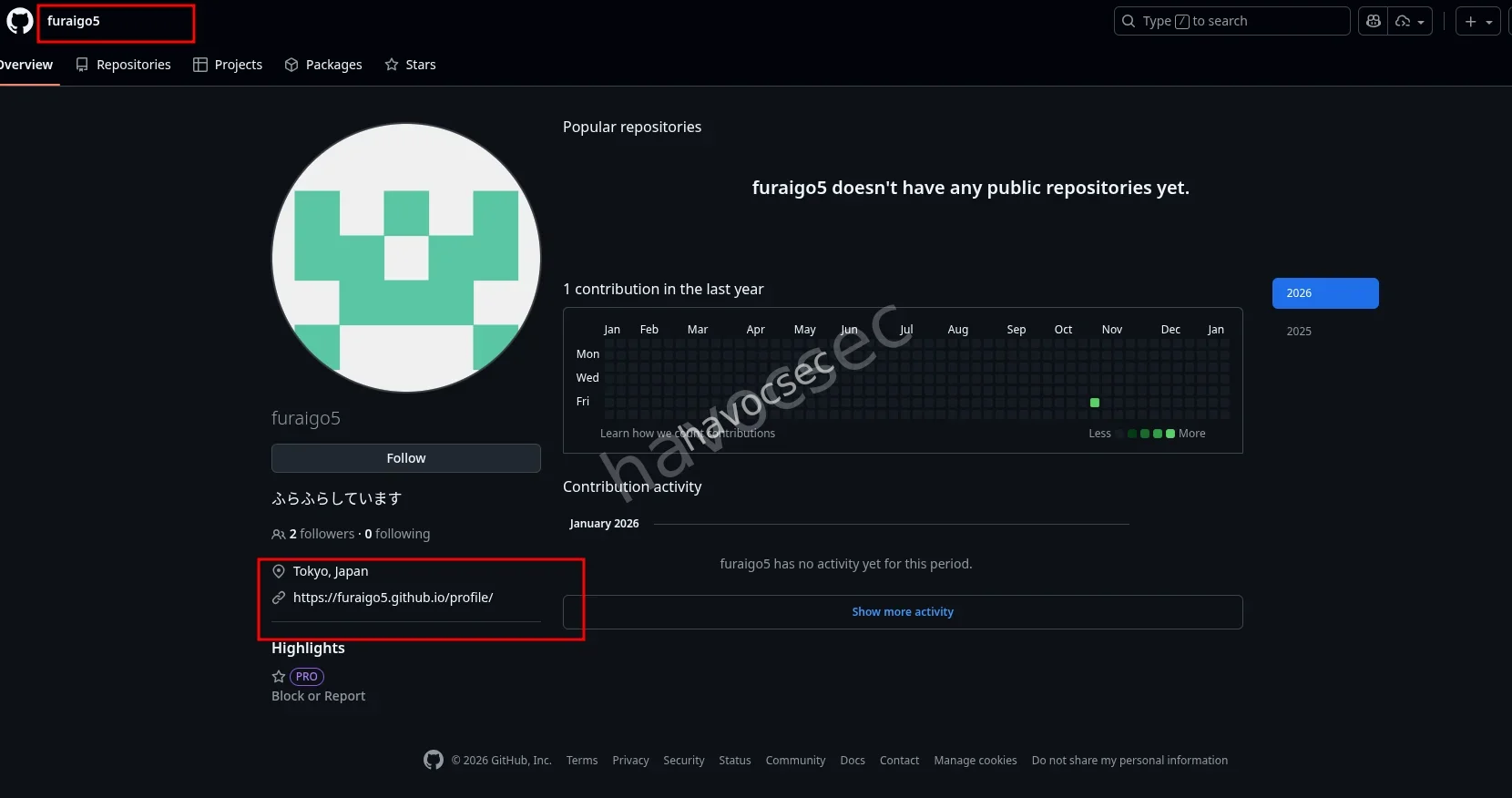
and then a link to a portfolio was there ,just waiting,which looked like this(the portfolio)
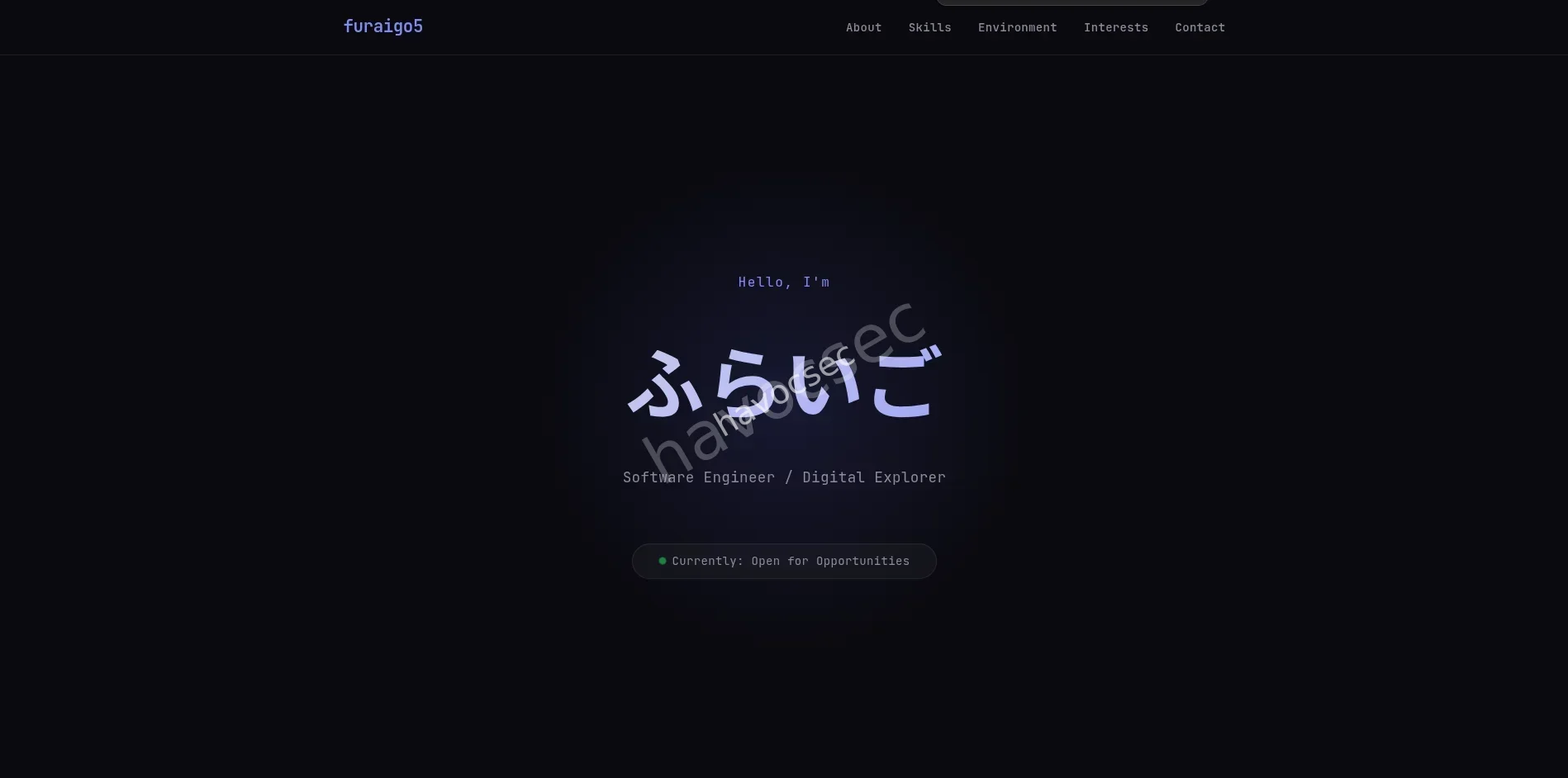
and bydhaway weve already gotten the flag which was the link so the flag is SWIMMER{https://furaigo5.github.io/profile/}
to the next one.
debeyohiru_03_email
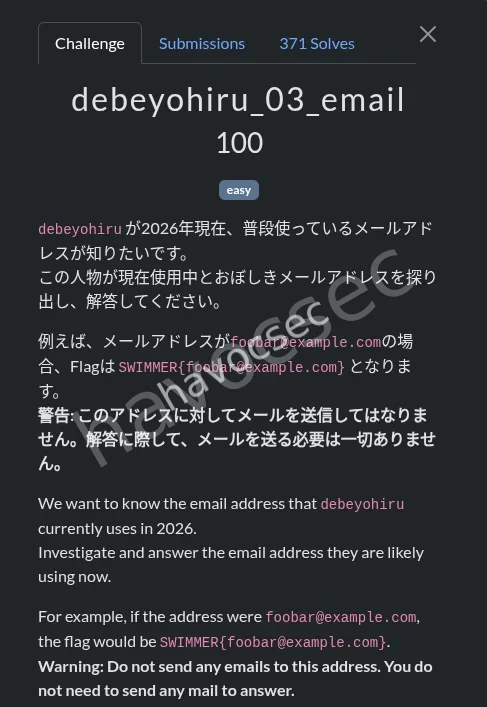
this was clear because we already have the portfolio so lets go to the contact page to look ,and it didnt dissapoint
and there it was just waiting for use thus the flag was SWIMMER{furaigo5.onionsoup@gmail.com}
boom!! to the next one…
debeyohiru_05_hidden1
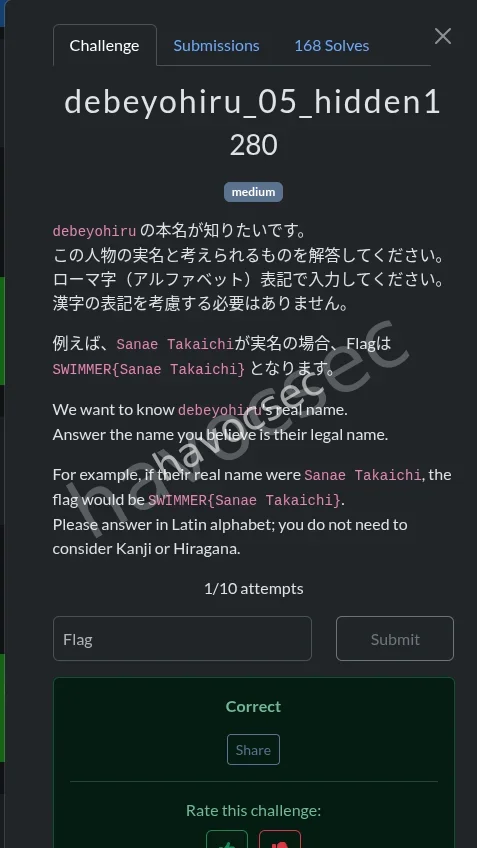
for this i searched like crazy but all in vain ,and then it dawned to me look into the code before quiting ?(laughs) and then there it was in the script.js file
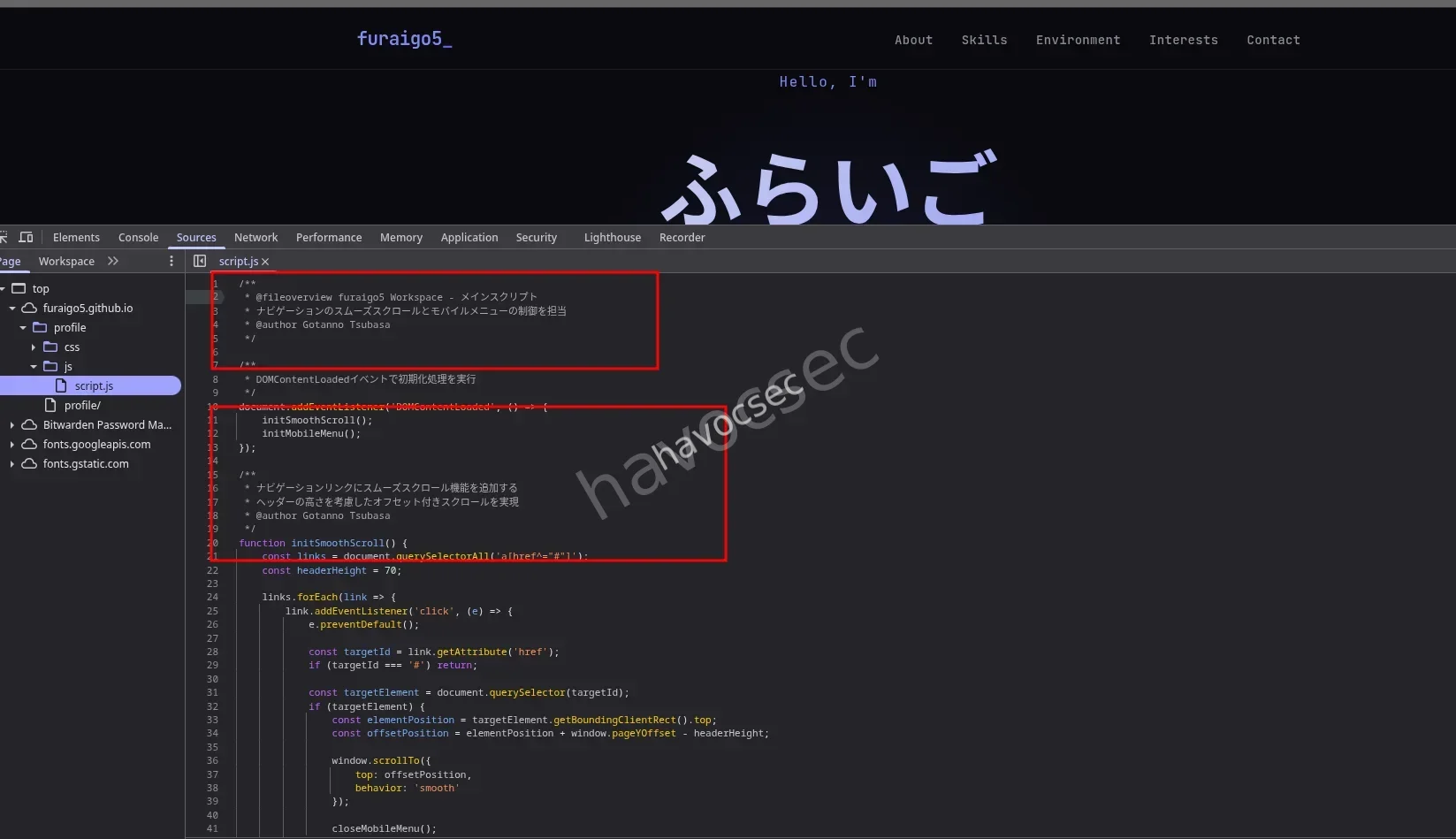
and some of the code is this
/**
* @fileoverview furaigo5 Workspace - メインスクリプト
* ナビゲーションのスムーズスクロールとモバイルメニューの制御を担当
* @author Gotanno Tsubasa
*/
/**
* DOMContentLoadedイベントで初期化処理を実行
*/
document.addEventListener('DOMContentLoaded', () => {
initSmoothScroll();
initMobileMenu();
});
/**
* ナビゲーションリンクにスムーズスクロール機能を追加する
* ヘッダーの高さを考慮したオフセット付きスクロールを実現
* @author Gotanno Tsubasa
*/
function initSmoothScroll() {
const links = document.querySelectorAll('a[href^="#"]');
const headerHeight = 70;
links.forEach(link => {
link.addEventListener('click', (e) => {
e.preventDefault();therefore giving me the correct flag SWIMMER{Gotanno Tsubasa}
to the next one
lilica_01_social
and there we go straight to x to look . and after doing a search we hit the jackpot
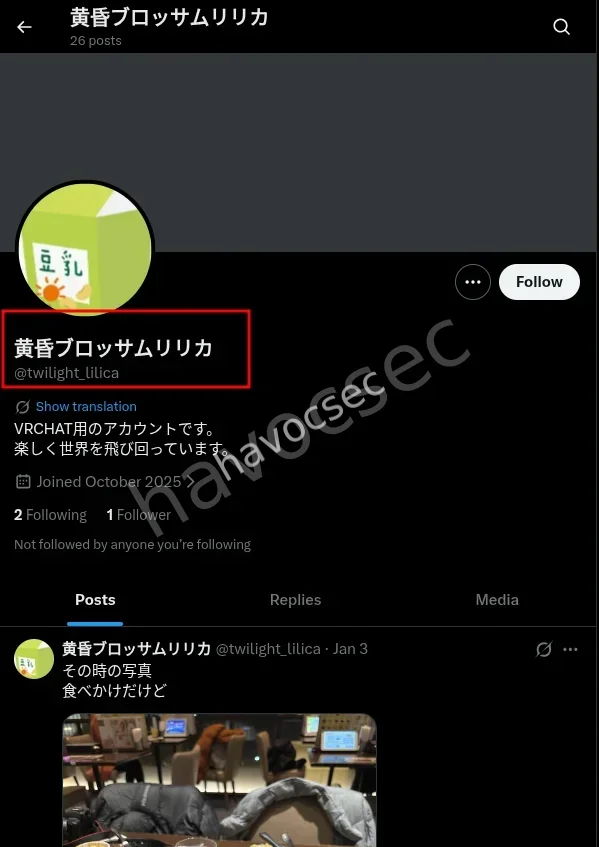
and there we had it the flag being SWIMMER{@twilight_lilica}
so as usual to the next challenge
lilica_02_virtual_identity
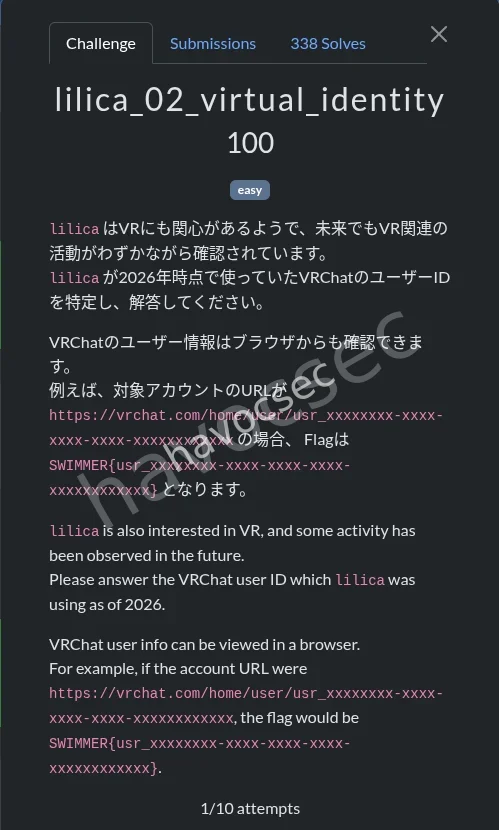
on the account in x we can see the words in the bio
This is an account for VRChat.
I’m happily flying around the world.
so we look into the vrchat to see if we can find our suspect account there and luck was on our side we got it
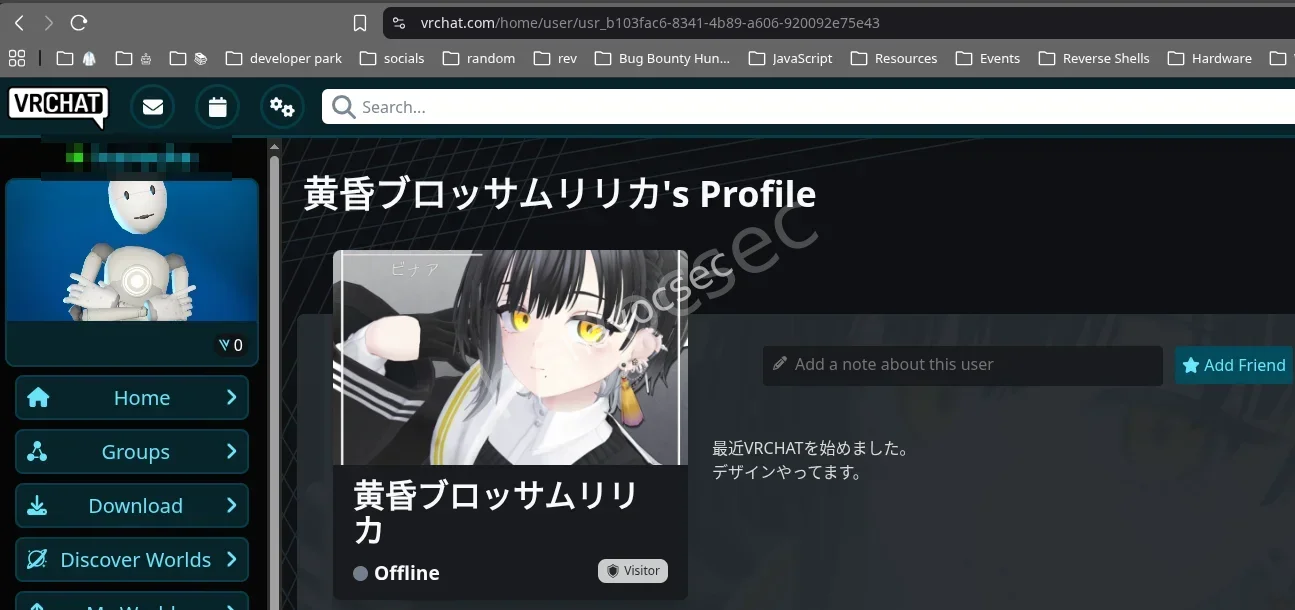
that being said looking at the adress bar we can see the link so we trim it to fir our flag format which is
SWIMMER{https://vrchat.com/home/user/usr_b103fac6-8341-4b89-a606-920092e75e43}
**a**and boom we had it.
now to the next challenge in the series…
lilica_03_virtual_world
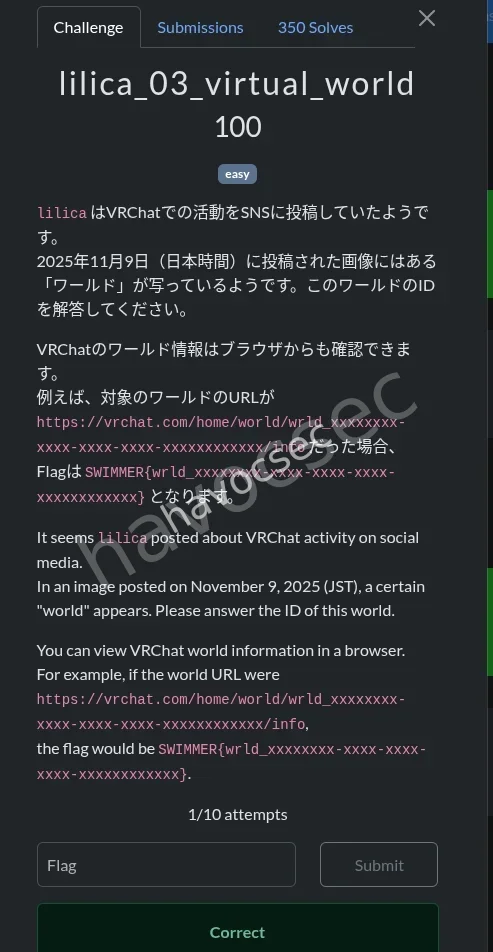
For this after we had the user account on vrchat we had to find the world they operate when here , so with the image posted on November 9, 2025 which is this

so i had chatgpt translate the words on the walls and it did pretty well in that and one of them was the nagisa to be precise this is what gpt told me
This world is clearly:
Japanese VRChat social room
and there i went to google and did that thing (a little search)
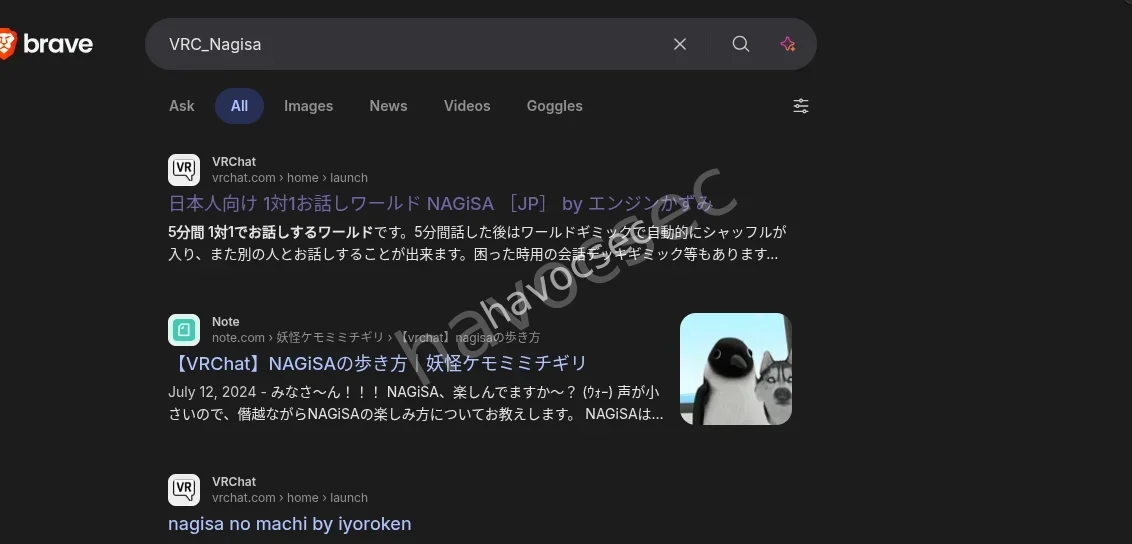
and there is a worlld by that name in vrchat so i clicked and it directed me to the world which looked cool bydhaway
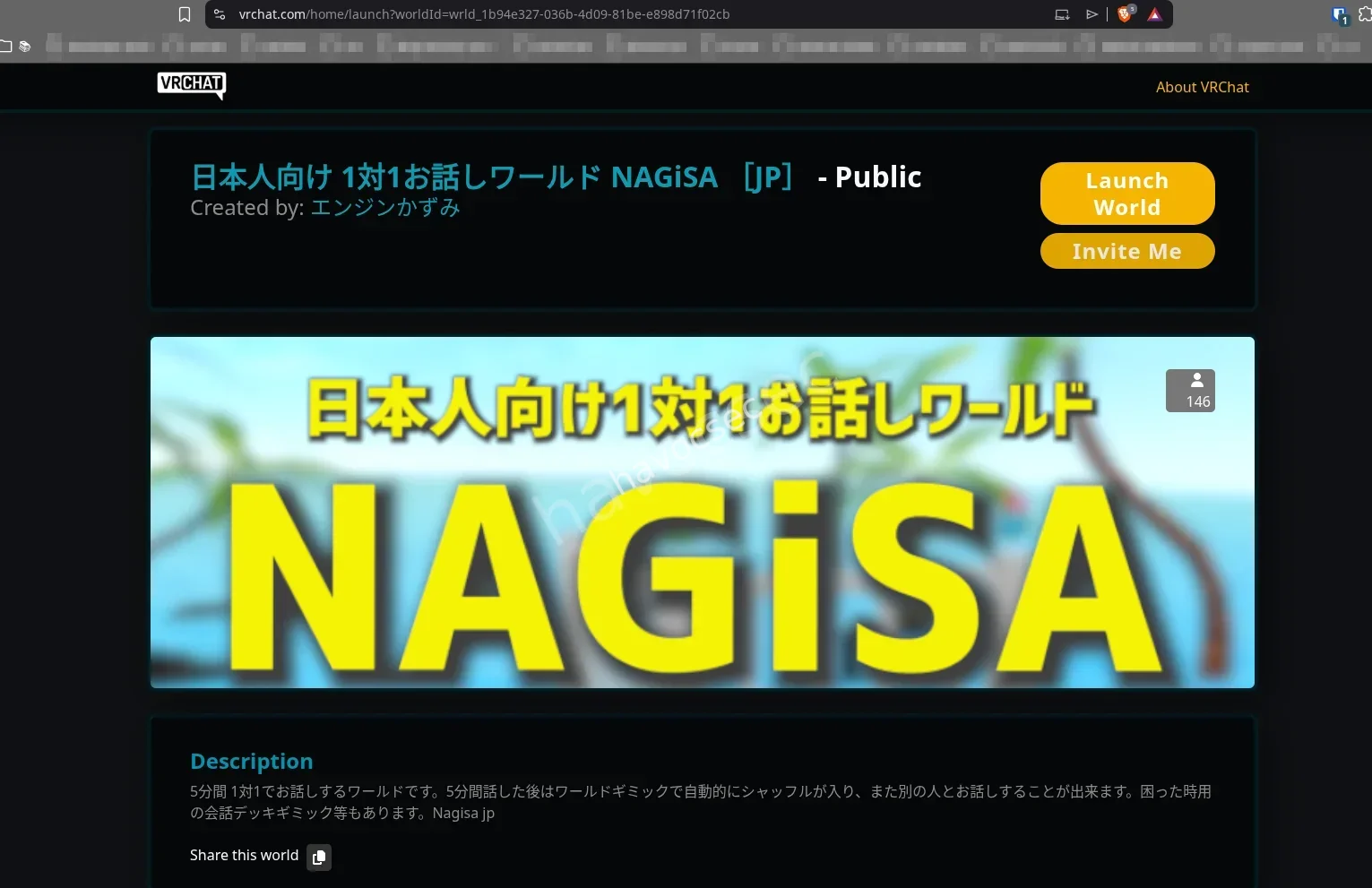
and there it was cool and precise.
therefore the flag being SWIMMER{wrld_1b94e327-036b-4d09-81be-e898d71f02cb}
to the next one
lilica_04_domain
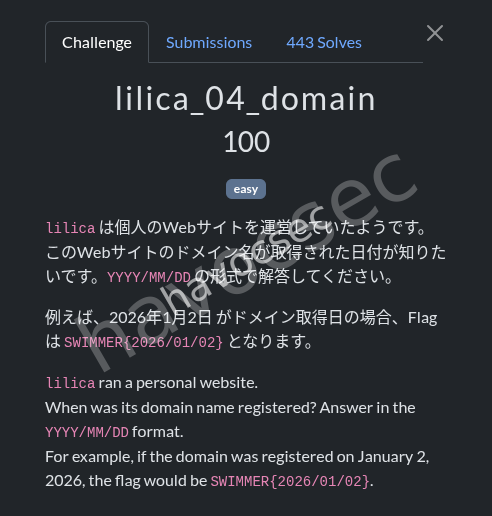
first of all the domain is on the x account the nigga posted it thats this twilight-lilica.com for this i had to go direct to whois and look for the date..
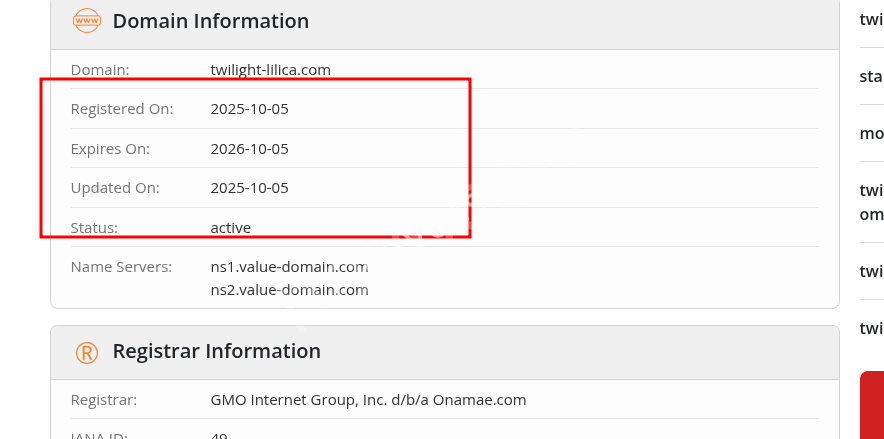
and there it was clean and juicy!!
SWIMMER{2025/10/05}
to the next one in the line
lilica_05_hosting
for this already we had a to do a little dig and we got some thing
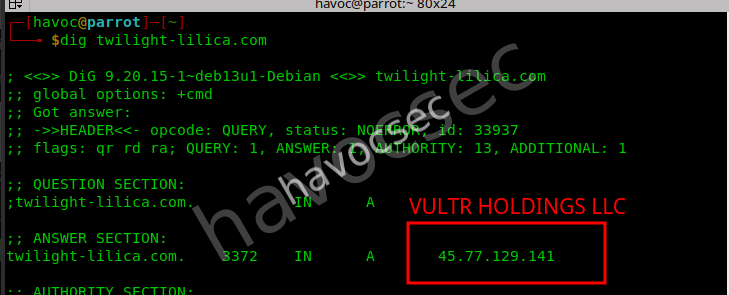
wooh that ip adress which is this 45.77.129.141 is owned by Vultr Holdings LLC. therefore looking onto it we got the email we needed and thats the flag which is SWIMMER{abuse@vultr.com}
and there we had it
now to the next one
cx
for this what we had to do was to do a simple search from what we were given ,so we did that and got the number which was pretty simple and the flag was SWIMMER{CX8100}
to the next one
pilot
for this we are given a photo and thats this

we had to find the name of the copilot as intructed and this is what we did
Research and Findings
-
Flight Identification: The “cx challenge” refers to Cathay Pacific (CX). Research into commemorative flights in Spring 2025 revealed that Flight CX8100 was a special tribute flight carried out on March 30, 2025, to commemorate the 100th anniversary of Kai Tak Airport.
-
Aircraft: The flight was operated using an Airbus A350-1000 (registration B-LXI).
-
Seat Identification: The attached image shows the cockpit of an Airbus A350, with an arrow pointing to the right-hand seat, which is the co-pilot’s seat.
-
Crew Details: The flight was commanded by a four-person crew. The primary pilots in the cockpit for the low-altitude fly-past were:
- Captain Geoffrey Lui (Chief Pilot, Airbus)
- Captain Adrian Scott (Flying Training Manager, Airbus)
-
Specific Seat Assignment: According to official Cathay Pacific documentary footage and social media posts from family members (e.g., Catherine Zhu), Captain Adrian Scott was the one co-piloting the aircraft from the right seat during this historic event.
Flag: SWIMMER{Adrian Scott}
to the next challenge.
flag_on_the_don
lets get into it
Challenge Overview
The objective was to identify a building in Gunma Prefecture that hosted a “Taiko no Tatsujin” (太鼓の達人) event on August 28, 2025, and provide its OpenStreetMap (OSM) way number.
Step 1: Event Identification
A search for events involving “Taiko no Tatsujin” in Gunma Prefecture on August 28, 2025, led to an official document from Shibukawa City.
- Event Name: Senior eSports Event (シニアeスポーツイベント)
- Date: August 28, 2025 (Thursday)
- Content: The event featured “Taiko no Tatsujin Donderful Festival” and “Gran Turismo 7” as part of a regional eSports promotion.
- Source: Shibukawa City Official Press Release (PDF)
Step 2: Venue Verification
The press release explicitly identified the venue:
- Venue: Shibukawa Civic Hall (渋川市民会館)
- Address: 2795 Shibukawa, Shibukawa City, Gunma Prefecture (群馬県渋川市渋川2795)
Step 3: Retrieving the OpenStreetMap Way Number
Using the OpenStreetMap search functionality for “渋川市民会館” (Shibukawa Civic Hall), the building was located. By selecting the building feature, the metadata revealed its unique OSM identifier.
- OSM Way ID: 628293186
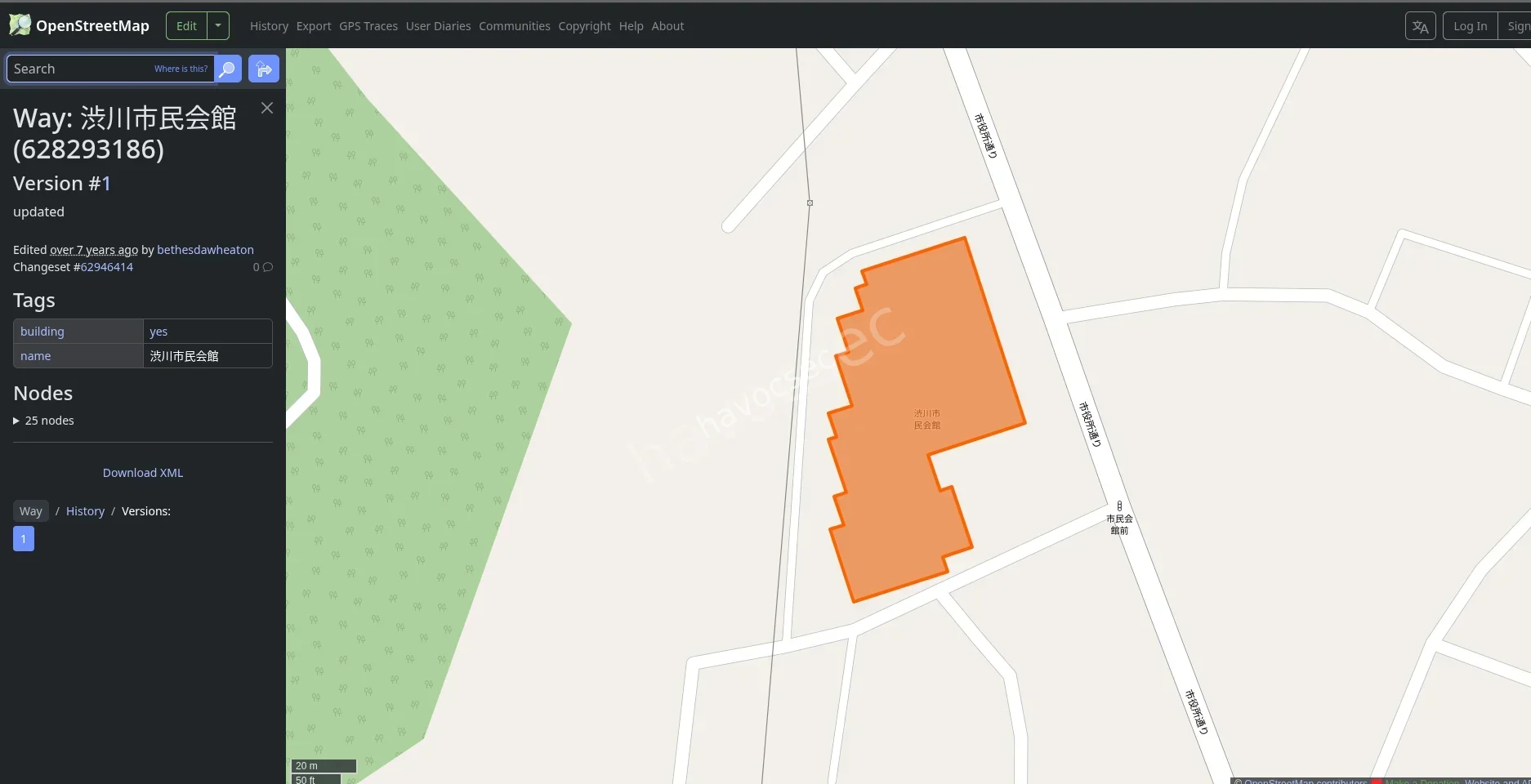
Final Result
Following the required flag format SWIMMER{way_number}:
Flag: SWIMMER{628293186}
to the next
truck
we did a good search and we got something juicy

i found a youtube link and also pictures on the internet which documents the odeal

but this website gave me the results i needed together with the youtube link
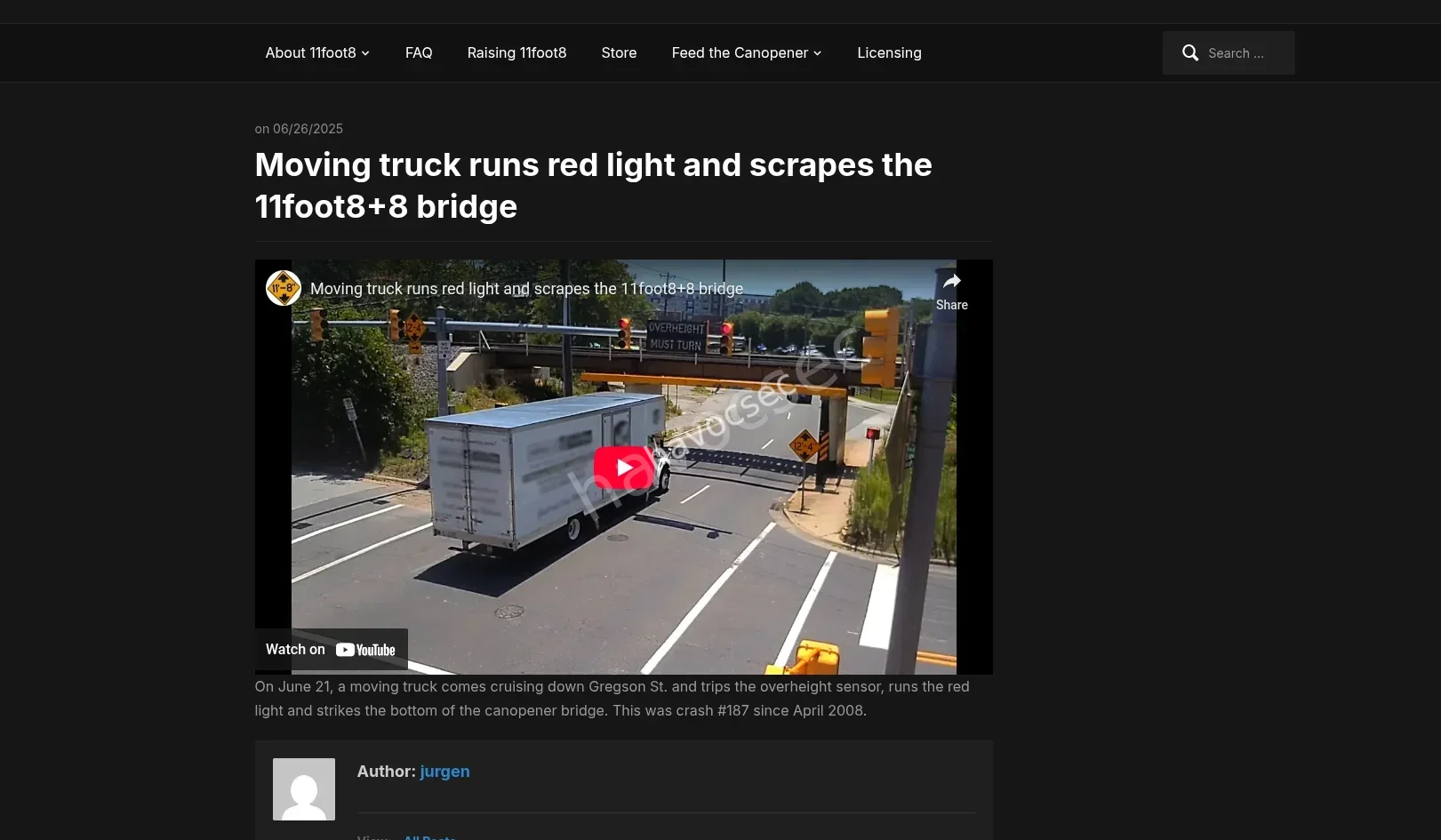
and there it was i saw the model of the lorry and did a little research and found the website which was also the link we needed

and there we had it
SWIMMER{www.miraclemoversusa.com}
on the lorry on the youtube video it was blurry but we got it.
so that was a few of the solved challenges but hope you enjoyed it
HAPPY HACKING!!

Comments